Jon AbbottHow To Prevent Ransomware
To prevent ransomware, you really need to look at all your cyber security because attackers have invested heavily to get past your defences
With the latest ransomware you really do not want the attackers to succeed. This is because historically they would just encrypt your data: whilst terrible, a modern backup solution can get you back on track quickly.
However, the latest versions either completely wipe your machines taking down your entire operation or copy some data before they start the encryption to use as ransom, or both as in the case of Travelex.
How Does It Get In?
There are many ways that Ransomware can infiltrate your network, the most common are:
- Spam / phishing email.
- Malicious website or web ad.
- Remote Desktop attack.
- Network vulnerability exploit.
- Weak passwords.
Failing to adequately protect against these vulnerabilities is classed as poor cyber hygiene: the basics of cyber security are not being maintained and weaknesses are created.
What the attacker is trying to achieve is to get you to run the malware; once the malware is running, they have control.
To prevent the latest versions of ransomware you must engage a multi-layered approach to your cyber security. You have probably heard this mentioned before but what does that really mean and why does it work?
Multi-Layered Approach
In the same way that you may have a lock, alarm, and cameras for your home security you need multiple cyber security measures for your business. This is critical, as the attack may come from many different angles and you want to stop it at the earliest opportunity. Remember that a failed attack may give the attacker enough information to exploit another vulnerability.
However, when thinking about this, I also like keeping it simple and think about the result they are trying to achieve. That is, they either want to hack into your email or run a malicious programme on your computer. To that end, they either need to exploit a vulnerability, trick you to give away your credentials or trick you to click on a link.
To give you an idea of what I mean, below is an example of an attempted phishing attack and the various defences you could, and I strongly recommend should, have in place. As you can see with a multi-layered approach there are many defence levels that can stop the attack in its tracks.

Defences In Detail
These are in a rough priority order however the reality is you really need all these defences to be installed, fully functional and checked to repeatedly defend against ransomware attacks.
Multi-Factor Authentication (MFA)
There are 300 million fraudulent sign-in attempts to Microsoft cloud services **every day **(at the time of writing) however 99.9% of them fail when MFA is enabled. The attacks are continuous and rising, the solution is simple and highly effective. If you have not got this enforced across your business I would probably stop reading now and get someone to do it.
The reason this prevents ransomware is if someone takes over your account, they can then send the ransomware to your colleagues, suppliers, and clients via email. As the email came from your mailbox it is more likely to bypass filters and the recipient will not suspect a virus.

DNS Protection
A common objective of a hacker is to get the victim to click on a malicious link. The best way to defend against this is DNS Protection. What this does it is verifies each website before you go to it and if it is malicious it does not let you visit that site. One of the best we have found is Cisco Umbrella, as it has many other features such botnet detection and IP level filtering.
In the WannaCry attack against the NHS there were two sites that were unaffected, these two sites were trialling Cisco Umbrella. We have been using it for over 6 years and I think it is more critical than malware protection.
Patch Management
Patch management simply means installing updates on software and hardware which will close a vulnerability that could be exploited by a hacker. For example a hacking group recently exploited two vulnerabilities to take down Travelex, one was on their VPN and the other was their Windows 10 machines. A simple solution to this for SME’s is to use a Cloud managed firewall like Cisco Meraki and Automox to patch your Windows, Linux, and Mac computers. The key is automation, do not think that you are going to be able to manually patch all your software and hardware.
Spam Filter
94% of malware is delivered via email, although all Spam filters are not perfect it is very sensible to invest in a 3rd party Spam filter that cannot be purchased by hackers. What I mean is to open an account they need a company number not just a credit card. This is one of the main issues with only having the Office 365 filtering. Anyone can open a 365 account and test the security, including hackers.
Training
Training your team about good password management, cyber hygiene and doing phishing training is extremely important. From reading this article you may have noticed that nearly all successful attacks require someone in your team to make a mistake. If they are well trained, they will not unintentionally help the attackers. However, the scams are ever evolving and some like vulnerability exploits do not need any human interaction to be successful, hence the need of a multi-layered approach.

Anti-Virus
The reason I left this item until last is as although it will help, this is essentially the last line of defence. If your antivirus is busy blocking attacks, your other defences are either not present or not working. Even though too many companies rely solely on antivirus to protect your business, it simply is not enough to prevent ransomware attacks. Therefore, have it on all machines, ensure that it is functioning correctly but do not pin your business’ protection on antivirus alone.
Cyber Hygiene Management
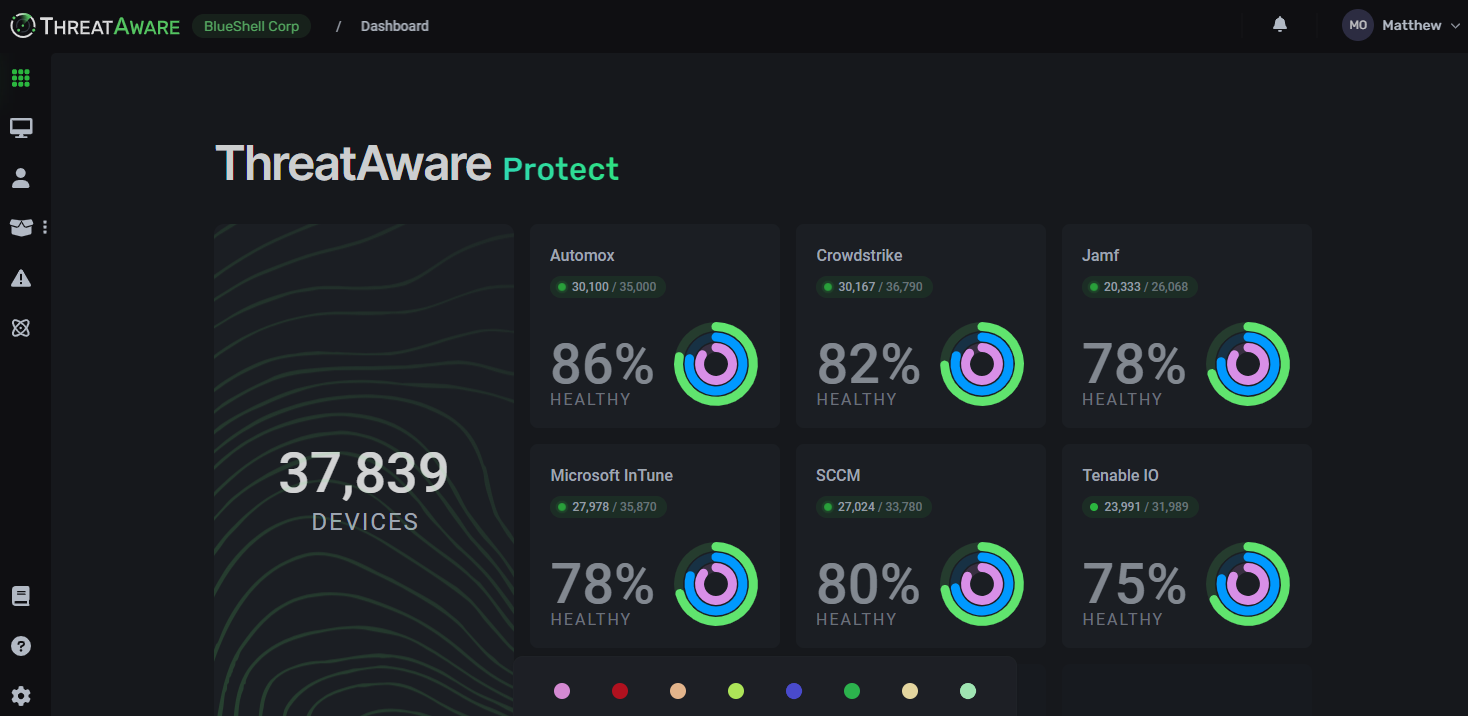
All the items I have listed are part of what is called cyber hygiene and to have good cyber hygiene all these defences always need to present and functioning correctly. With a Cyber Hygiene management platform such as ThreatAware this task is quickly and easily achieved due to its clear reporting and agentless design.
Wrap Up
I hope this article has given you a clear picture of the best way to prevent a ransomware attack. Additionally, I hope that it highlighted some defences that you were either unaware of entirely or you did not appreciate their purpose. If you want some more help with improving your cyber hygiene and therefore your defence against ransomware, please do reach out.
Ready to protect all your assets?
Leveraging its proprietary timeline-matching technology, ThreatAware ensures you have a complete, accurate, and non-duplicated asset inventory in real-time. No more guesswork – spot and fix deficiencies across your entire IT estate instantly.
Onboard in less than 30 minutes.
Request a Trial