Cybersecurity Simplified
Discover & Protect Every Cyber Asset
Regardless of cyber asset management maturity level, we have a solution that will fit your needs for today and tomorrow.
- Connect.
- ThreatAware Connect is our entry level offering, connecting to your current tools via API and obtaining security data directly from each one. Our unique matching algorithms then generates a highly accurate cyber asset list. This is ideal for organisations with fewer than 100 assets, or those with a restricted budget to take the first step on the road to complete breach protection.
- Discover.
- Discover validates not only deployment of security tools, but its functional status. It shows you where controls are inactive and gives you full inventory information on all devices. Discover allows you to dynamically tag your devices to align your inventory to match your organisation's structure.
- Protect.
- Protect is for organisations who already have a clear picture of their cyber assets and need to ensure that their cybersecurity controls are actually functioning on each device, and are in a healthy state. This is ideal for organisations who adhere to NIST, ISO 27001 or similar frameworks.
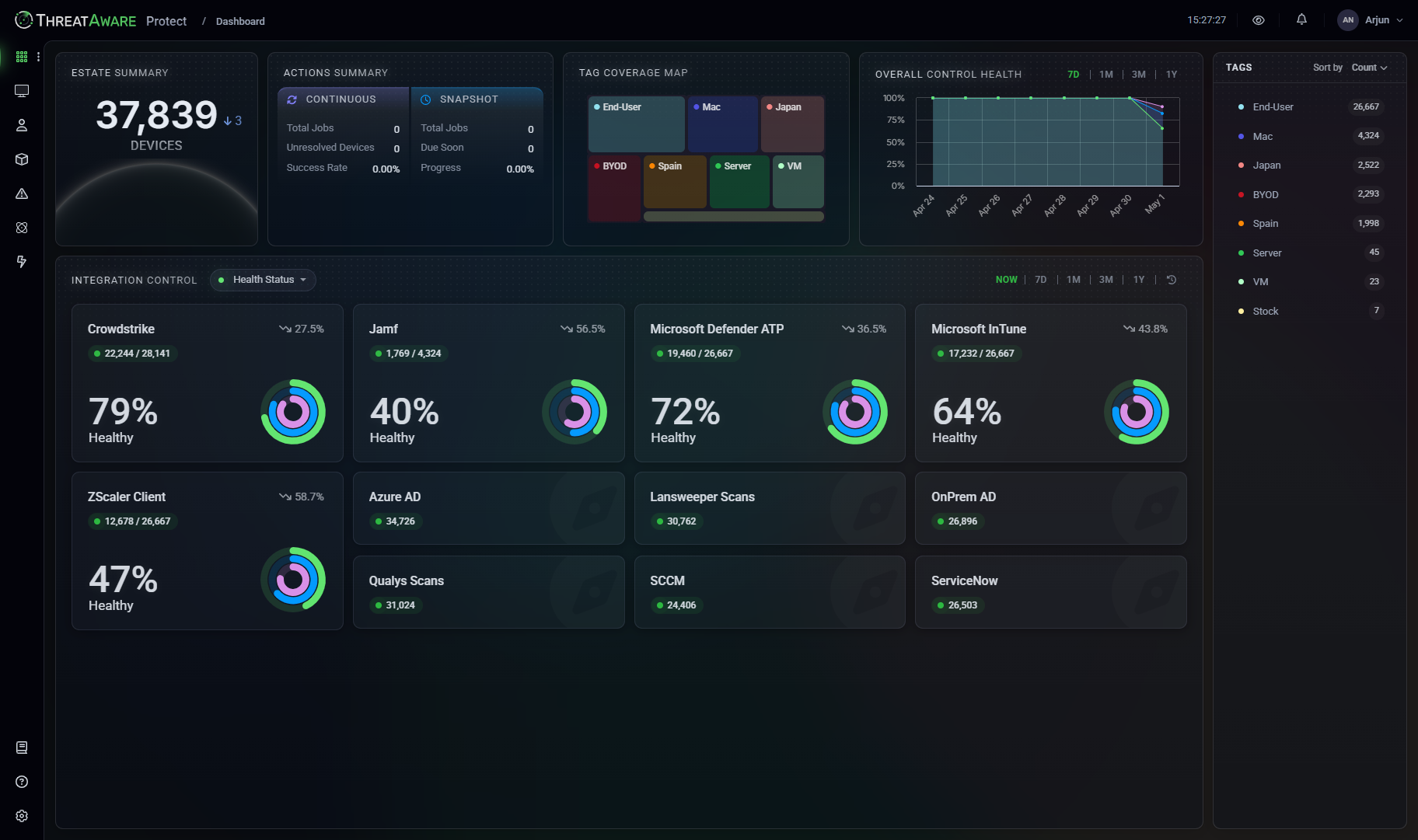
No more spreadsheets
ThreatAware Connect
ThreatAware Connect is for organisations that want to start managing their cyber assets in a better way. You can do away with manually exporting lists and struggling to match your cyber asset data. Using our API connections and time-line matching algorithms you will finally have a single source of truth you can rely on.
- API Powered.
- No need to install anything, simply connect to your existing tools via API.
- Unrivalled Matching.
- ThreatAware's matching engine ensure that you have a single source of truth.
- Automatically Updated.
- Connect refreshes your cyber assets from source continuously, every hour.
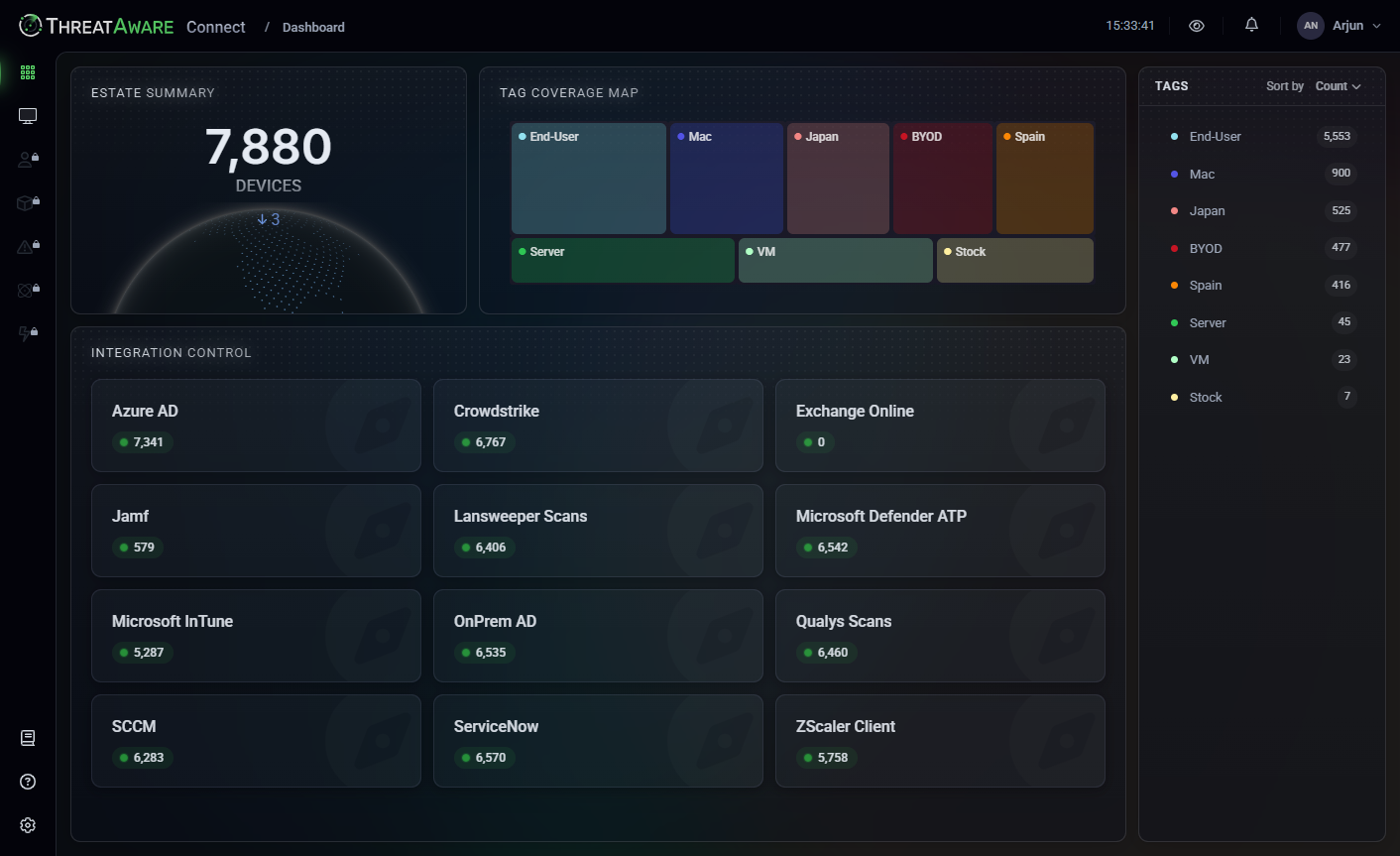
Uncover more
ThreatAware Discover
Discover addresses two cornerstones of Cyber Asset Management. These are if the security controls are deployed and functioning. You can update the data in real-time to ensure that your coverage is complete.
- Agentless Design.
- Connects via API to all of your existing Cyber Security Controls.
- Active Monitor.
- Detects if the security controls are responding back to their consoles.
- Real-time Accuracy.
- The data can be refreshed on-demand to ensure your coverage is complete.
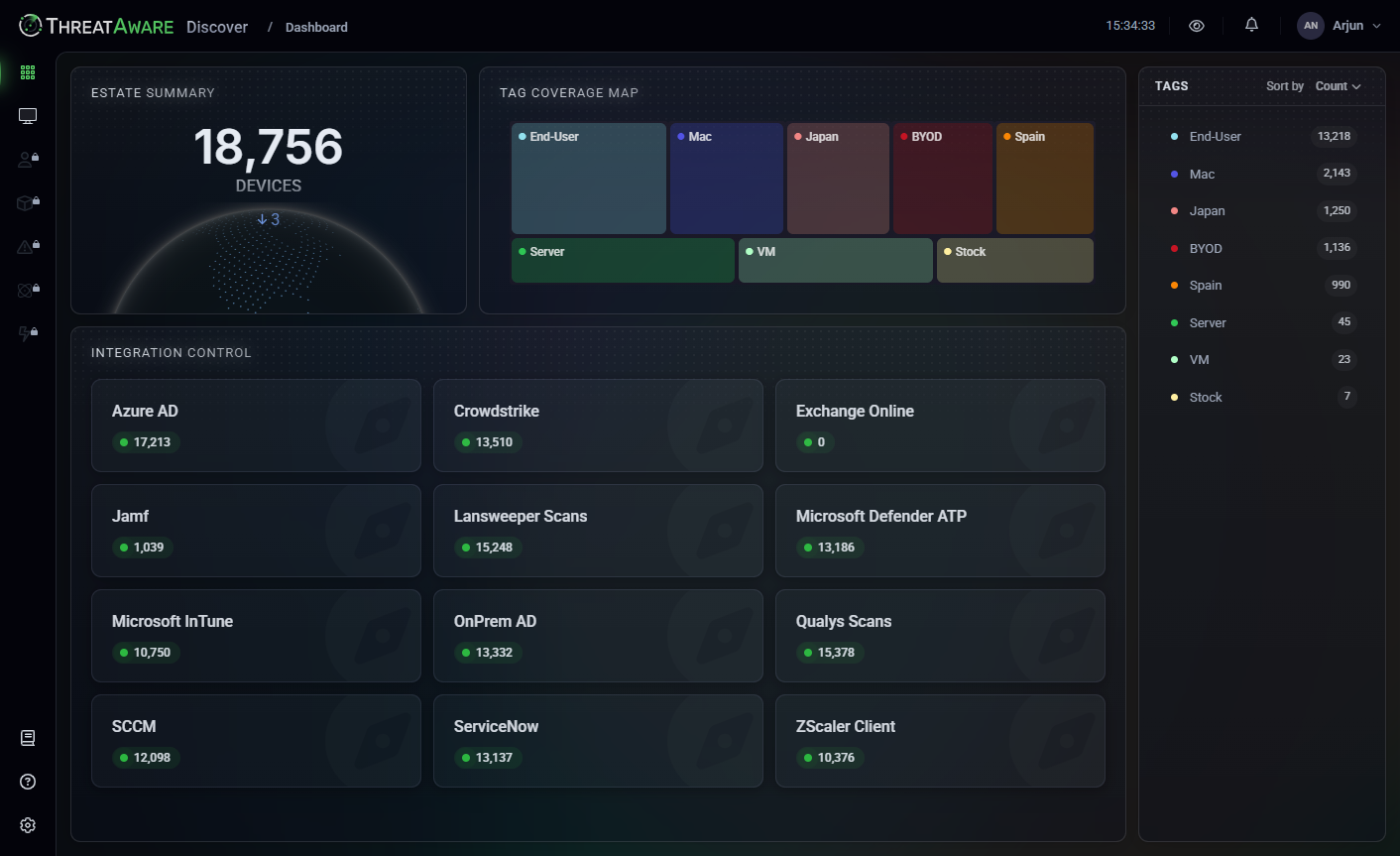
Be sure
ThreatAware Protect
Gain true insight into the status of every control that is protecting your devices. Are the controls, deployed, functioning and healthy. See the data in context to quickly focus on the high priority issues.
- Agentless Design.
- Connects via API to all of your existing Cyber Security Controls.
- Granular Control Monitoring.
- Instantly get the overall health of every security control in one single screen.
- Finely Tuned.
- Protect can be highly customised to mirror your organisation's control policies. Monitor what matters to you.