Beyond Cyber
Use Cases
ThreatAware delivers benefits that extend beyond the cybersecurity team, empowering company boards to better understand and manage cyber risks, while enabling procurement teams to streamline device lifecycle management.
IT Asset Management
Discover how ThreatAware's API discovery, time-matching, and dynamic configuration elevate asset management to the next level.
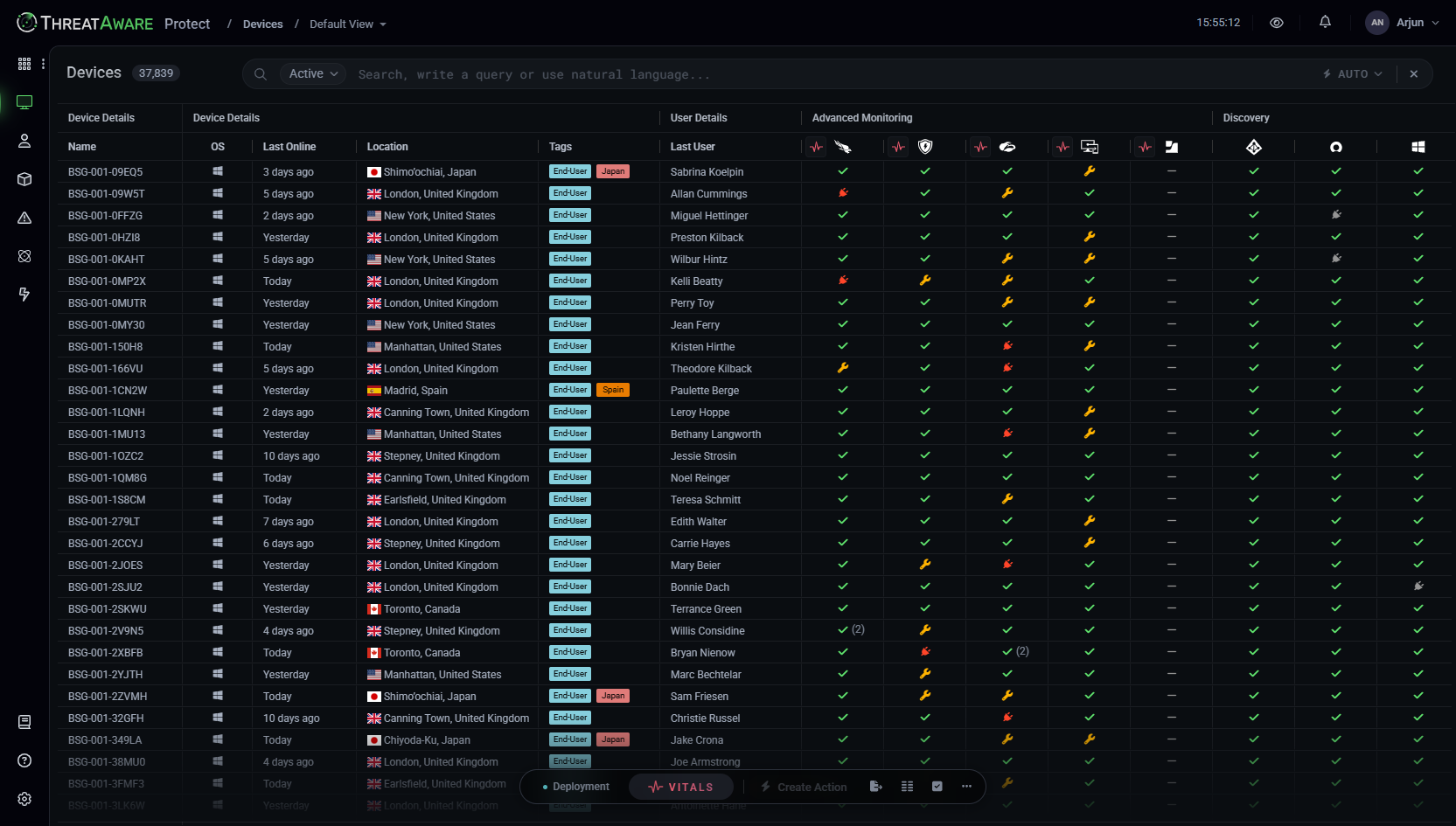
Cyber Hygiene
Find out how ThreatAware can help you efficiently and continuously monitor the status of your estate's controls.
Cyber Asset Attack Surface Management
Explore how ThreatAware can highlight gaps in your attack surface and help you reduce them.

Cyber Risk Reporting
Learn how ThreatAware can support you in generating accurate, user-friendly cyber risk reports to help drive change and mitigate risks.
ThreatAware has transformed the way leading organisations secure their cyber assets worldwide
"The platform provides us with a clear, real-time view of our assets and compliance status and gives us confidence that we have a single source of truth for our fleet of security agents."
Abraham Ingersoll, Chief Security Officer, The Hut Group