Charlie WescombeSecuring AI Initiatives
Why Your Security Programme Needs to Evolve for the AI Era
Join us at the Gartner Security & Risk Management Summit in London to discuss how security leaders are navigating these challenges in practice.
As organisations expand their technology environments, security teams face a critical challenge: how do you secure what you can't see? According to IBM's Cost of a Data Breach Report, 35% of breaches involved shadow data, highlighting the growing challenge of unmanaged data sources across IT environments.
The Security of AI isn't just about protecting AI models, it's about ensuring your entire security infrastructure can adapt to rapidly changing technology landscapes. Data stored across multiple environments accounted for 40% of breaches and took an average of 283 days to identify and contain, compared to 224 days for on-premises data.
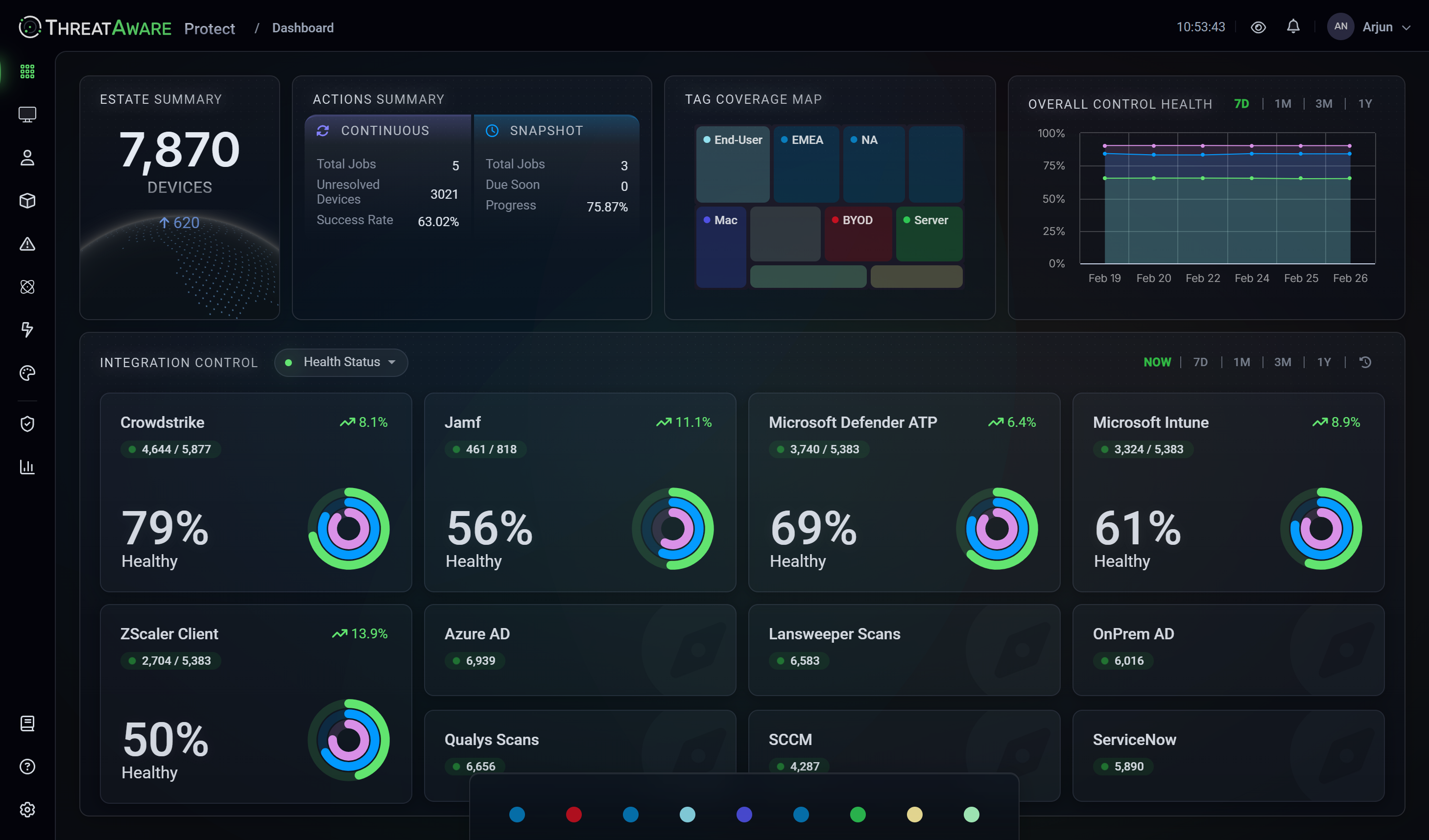
Three key areas where ThreatAware supports AI-era security:
Discovery of Unknown Assets: Our platform identifies every device accessing corporate data. Organisations typically discover 30% more devices accessing corporate systems than previously known.
Continuous Security Validation: Real-time monitoring ensures security controls remain effective as AI workloads scale and change, preventing the misconfigurations that create dangerous gaps.
Automated Risk Response: Custom workflows can automatically flag and remediate security gaps, ensuring governance keeps pace with innovation.

Secure Every Device in Your Network
Instantly uncover and protect every asset in your IT estate with ThreatAware.
Identify unknown devices, reconcile asset data across platforms, and eliminate security gaps to ensure continuous cyber hygiene.
Book a Demo