IT Asset Management
Despite an increase in investment in cyber security and IT, most organisations still experience significant gaps in their understanding of their full IT environment. Traditional methods like agent-based tools often fall short when it comes to accurate and digestible data. Through our platform, organisations discover that up to 10% of their devices lack essential security controls, while 15% have gaps in endpoint protection.
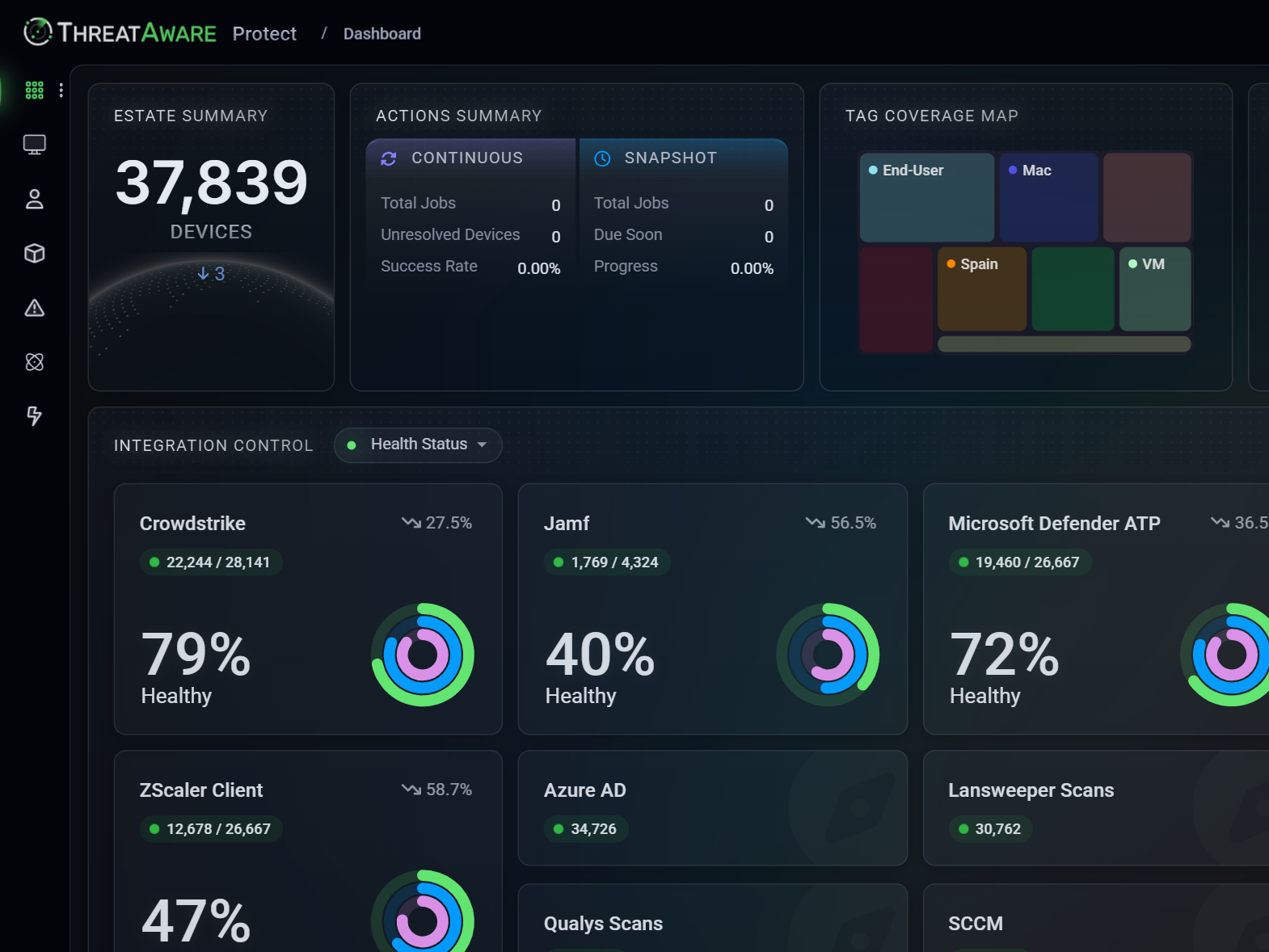
ThreatAware gathers data directly from all your security tools' cloud consoles and delivers a contextualised single view of your entire estate, with implementation taking under 30 minutes.





Key Benefits
Drive Efficiency and Strengthen Security
Empower IT teams with full asset visibility, streamlined management, and seamless regulatory compliance for optimal performance and protection.
"The platform provides us with a clear, real-time view of our assets and compliance status, and gives us confidence that we have a single source of truth for our fleet of security agents."
- Improved IT Service Delivery Gain full visibility of all assets and their configurations, enabling IT teams to proactively monitor, manage, and maintain systems for optimal performance and up-to-date operations.
- Enhanced Data Security Track and monitor IT assets to quickly detect unauthorised access or suspicious activity, enabling swift identification and mitigation of security threats.
- Strengthened Regulatory Compliance Ensure compliance with industry regulations by keeping assets properly configured, securely deployed, and fully tracked for seamless audits and reporting.
Key Features
Enhance Security with Intelligent Automation
Transform your cybersecurity management with seamless integration and automated workflows for comprehensive asset protection.
- Security Tool Integration Connect and enhance your existing security tools through seamless API integration, providing accurate, real-time visibility across your entire asset landscape.
- Intelligent Workflow Automation Streamline your security response with automated workflows that handle everything from compliance alerts to complex remediation processes, ensuring swift action on potential vulnerabilities.
- Advanced Security Validation Monitor and validate security controls across your estate, with real-time tracking of critical security measures including endpoint protection, patch status, and multi-factor authentication deployment.
ThreatAware has transformed the way leading organisations secure their cyber assets worldwide
"The platform provides us with a clear, real-time view of our assets and compliance status and gives us confidence that we have a single source of truth for our fleet of security agents."
Abraham Ingersoll, Chief Security Officer, The Hut Group