Cyber Asset Attack Surface Management (CAASM)
To fully comprehend your cyber-attack surface, an accurate comprehensive asset inventory is essential — but it's only the starting point. ThreatAware goes beyond simple inventory management, delivering deep insights into the security posture. The platform provides complete visibility of your IT environment, identifies key vulnerabilities and prioritises actions for your team. Our customers typically discover 10% of their total devices lack essential security controls - devices that were previously invisible to their security teams.
Cyber Asset Attack Surface Management enables organisations to consolidate assets distributed across their expanding IT environments, strengthening your security foundation.





Key Benefits
Comprehensive Visibility and Swift Incident Response
Detect every asset, streamline lifecycle management, and respond to threats faster with real-time insights.
"ThreatAware's ability to automate and centralise asset management has been pivotal in enhancing THG's cybersecurity resilience, providing peace of mind and allowing the team to focus on strategic initiatives rather than reactive and manual tasks."
- Achieve Full Visibility Detect and identify every asset on your network, ensuring no attack vectors are missed.
- Streamline Asset Lifecycle Management Use real-time data to quickly identify and isolate compromised assets, reducing response times and minimising the impact of threats.
- Enhance Incident Response Speed By eliminating the need for manual processes, your team can focus on proactive measures, streamlining workflows and ensuring faster resolution of security incidents.
Key Features
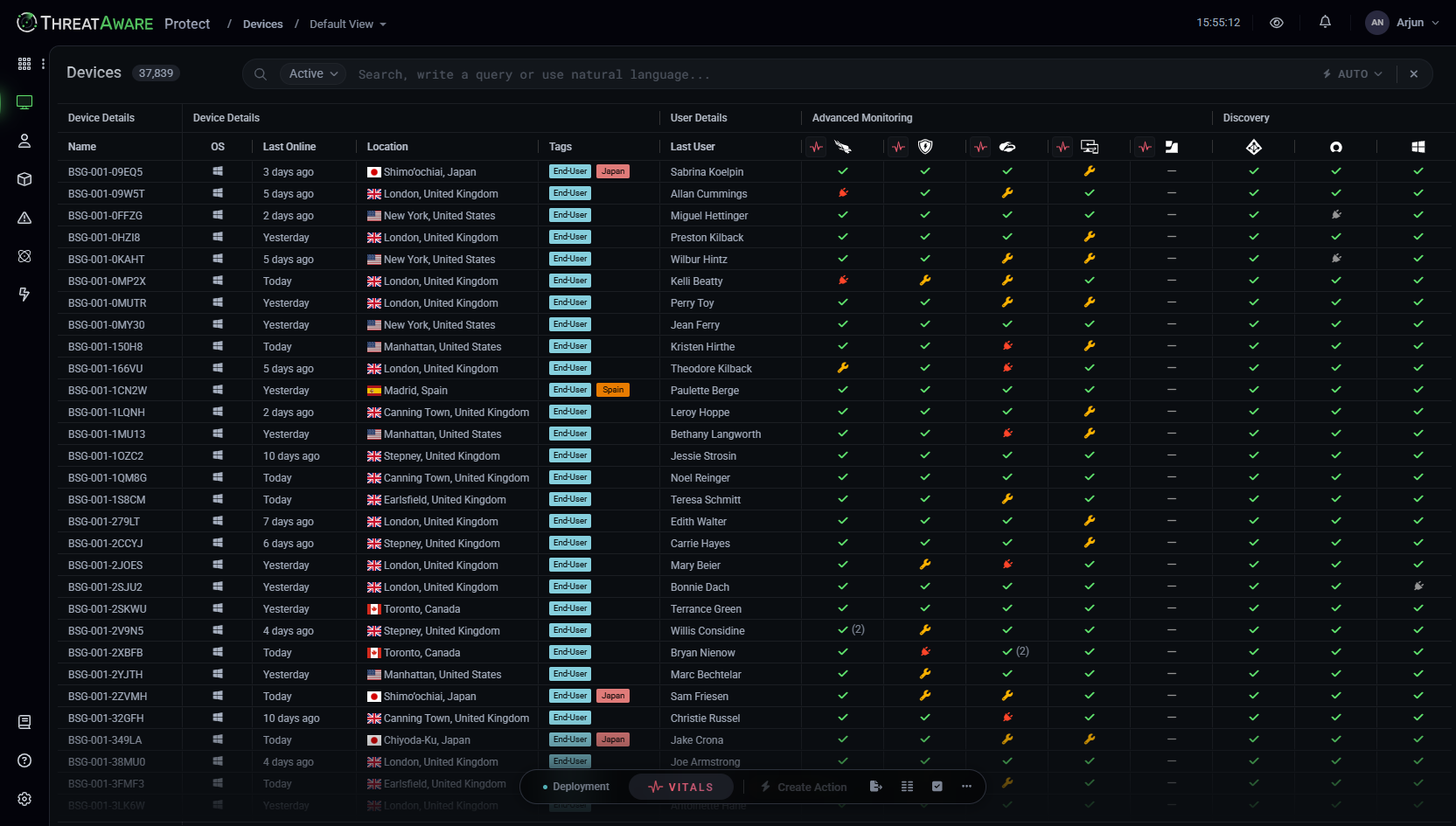
Comprehensive Cyber Asset Management
Gain full visibility, prioritise vulnerabilities, and streamline insights with advanced visualisation, dashboards, and asset querying.
- Attack Surface Visualisation Gain full visibility of all cyber assets, including devices, users, and software. Easily filter and prioritise the most vulnerable assets to protect your organisation from potential threats.
- Dynamic Dashboards Instantly access insights with a pre-built home dashboard or customise dashboards that can align with upcoming audits and device priorities. This provides one consolidated page for frequent queries and actionable tailored data.
- Comprehensive Asset Querying Perform fast, in-depth searches across extensive datasets, covering a wide range of devices and security systems. Efficiently locate and analyse the assets you need to keep your network secure.
ThreatAware has transformed the way leading organisations secure their cyber assets worldwide
"The platform provides us with a clear, real-time view of our assets and compliance status and gives us confidence that we have a single source of truth for our fleet of security agents."
Abraham Ingersoll, Chief Security Officer, The Hut Group