Cybersecurity Simplified
Discover & Protect Every Cyber Asset
Regardless of cyber asset management maturity level, we have a solution that will fit your needs for today and tomorrow.
Discover Every Asset
ThreatAware Connect
Connect transforms how organisations discover and track their cyber assets. Our patent-pending timeline matching technology uncovers devices that traditional methods miss, providing complete visibility across your corporate network.
- Breakthrough Asset Discovery
- Timeline matching technology creates unique device fingerprints, discovering 20% more assets than conventional methods whilst eliminating duplicate records.
- Agentless by Design
- API connections to your existing tools provide complete visibility without performance impact or complex deployments.
- Real-Time Intelligence
- Continuous 60-minute updates ensure your asset inventory stays current as devices join, leave, and change across your environment.
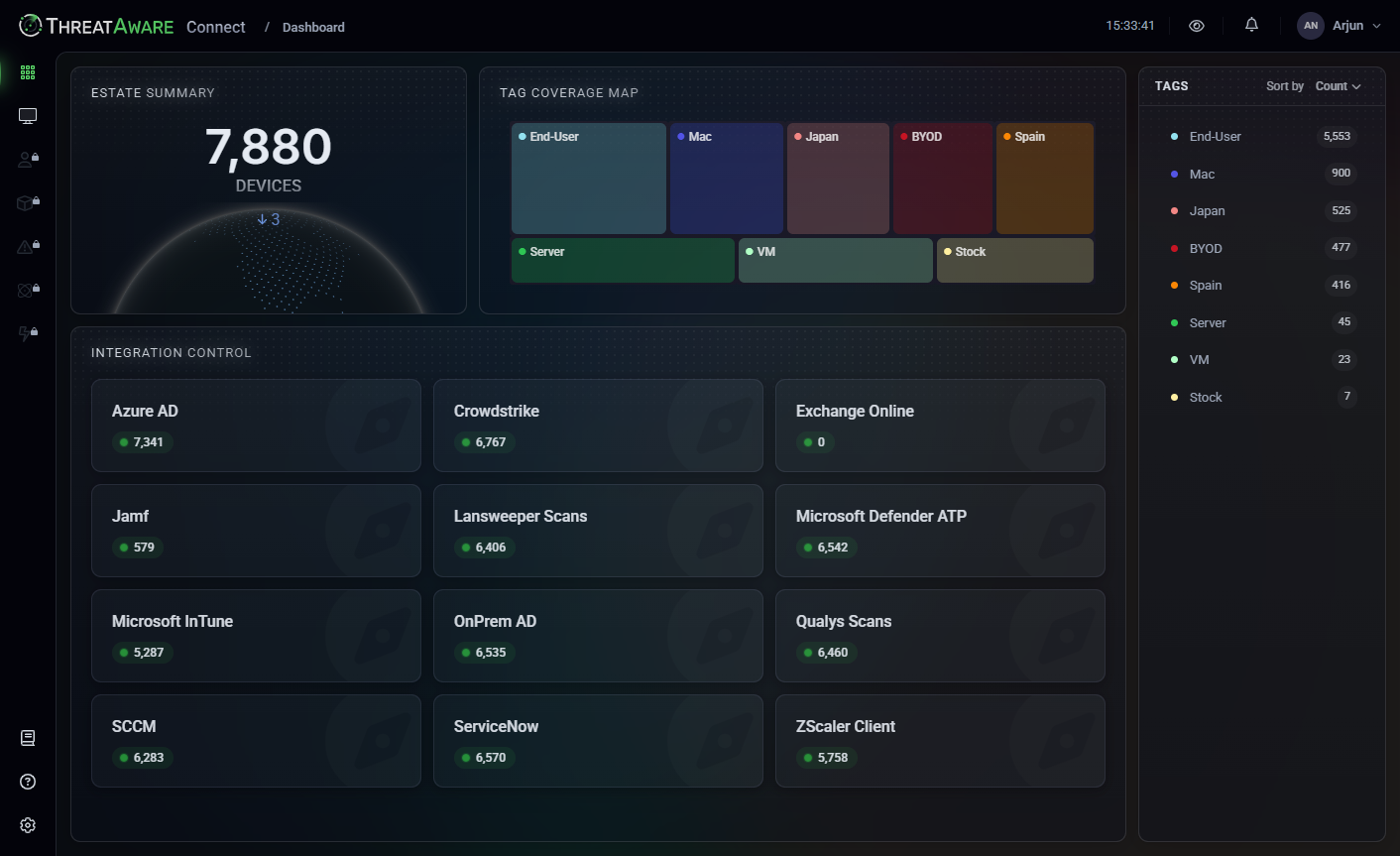
ThreatAware Connect enhances IT Asset Management by offering real-time insights into asset status.
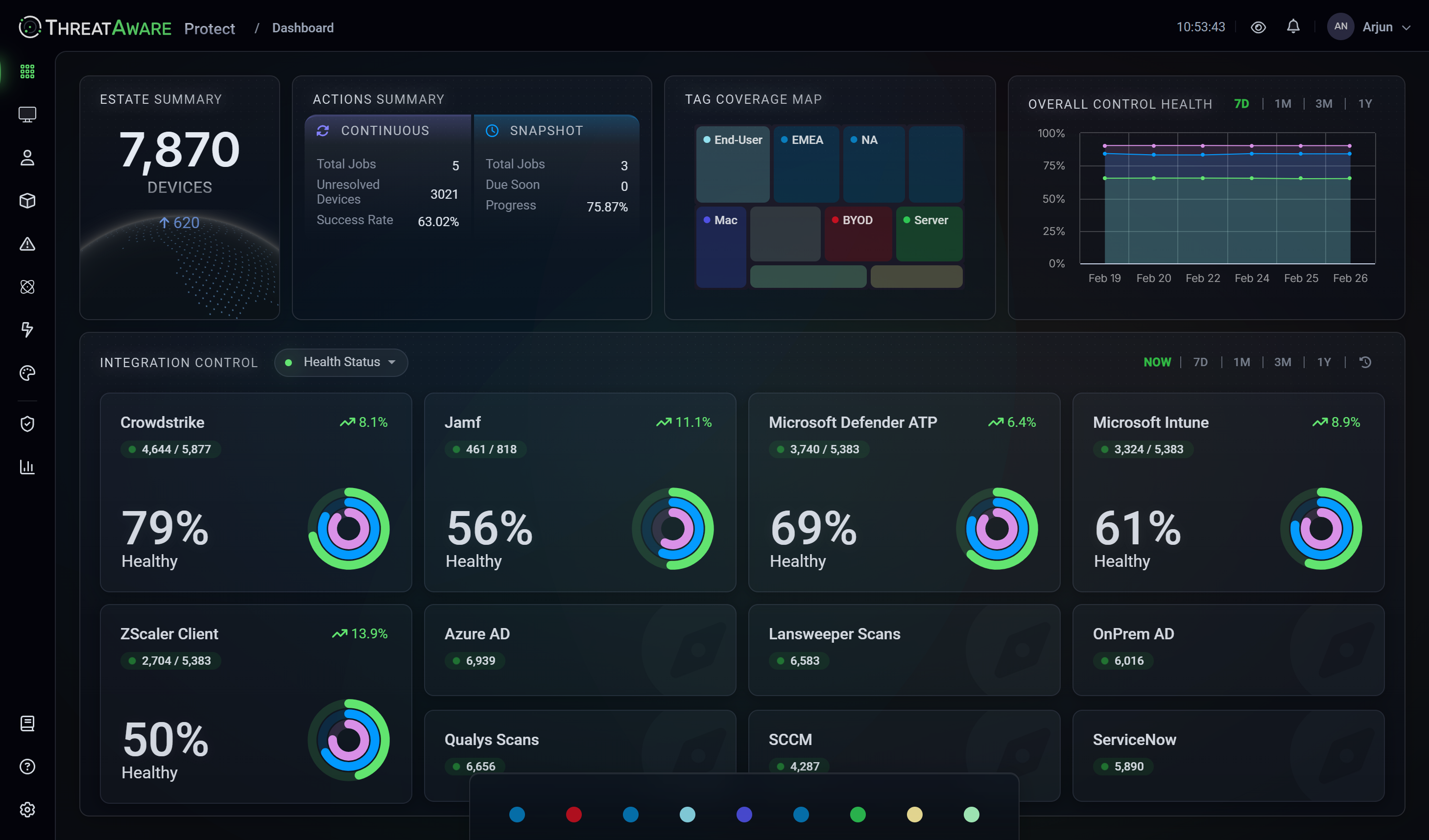
Validate Every Control
ThreatAware Discover
Discover addresses the critical question: are your security controls actually working? Our platform validates deployment, functionality, and health across every device, transforming security blind spots into actionable intelligence with automated risk prioritisation.
- Complete Control Validation
- Instantly verify that security tools are deployed, functioning, and properly configured across your entire estate.
- Intelligent Risk Scoring
- Advanced analysis identifies high-priority vulnerabilities and misconfigurations, focusing your team's efforts where they matter most.
- Continuous Health Monitoring
- Real-time validation ensures your security posture remains strong as your environment evolves.
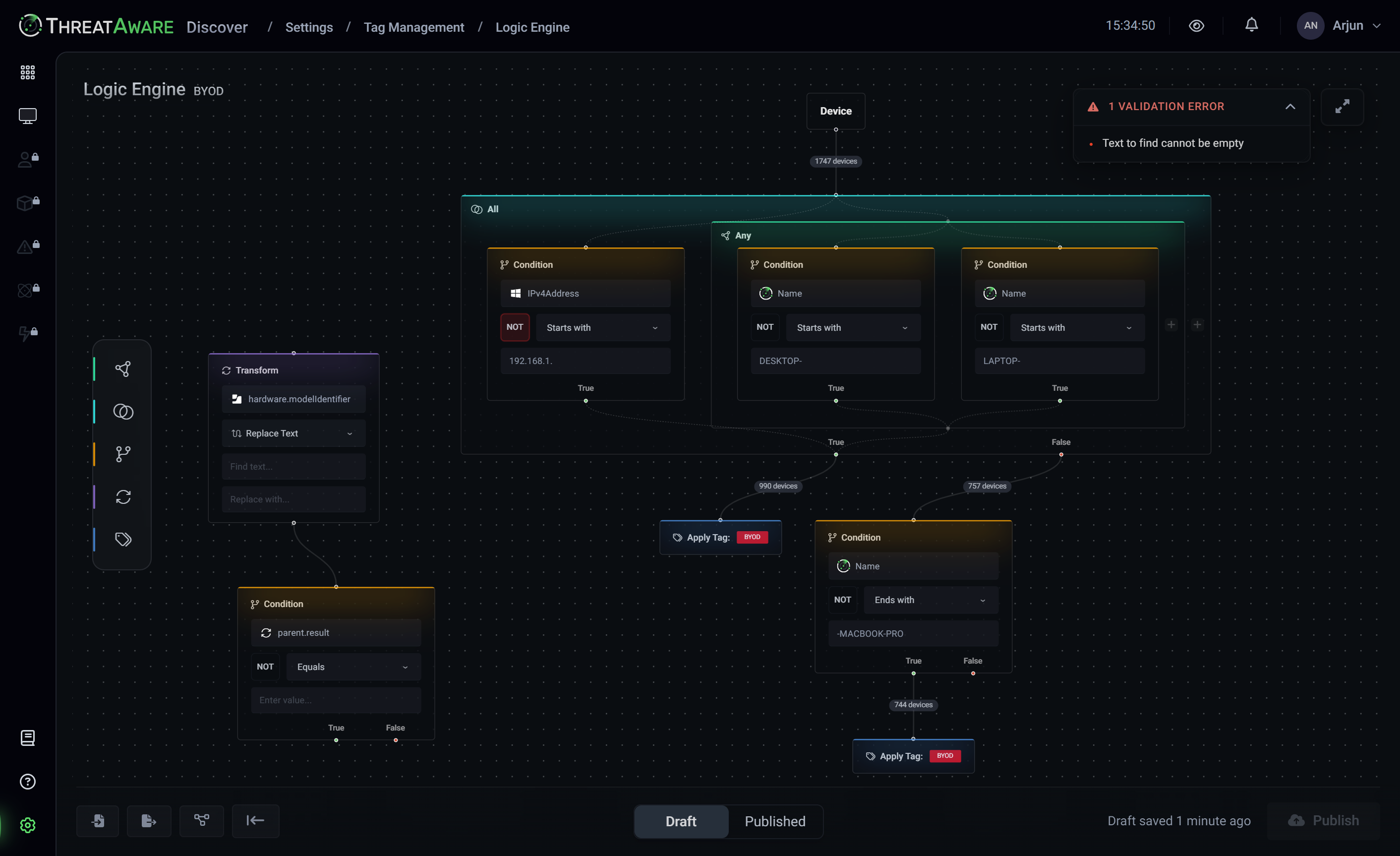
Our solutions address Cyber Asset Attack Surface Management, providing a unified view of your IT environment.
Automate Every Response
ThreatAware Protect
Protect closes the security loop by transforming insights into automated actions. Our Action Centre orchestrates remediation workflows across your security stack, whilst custom Logic Engine rules enable sophisticated risk management tailored to your organisation's unique requirements.
- Automated Remediation Workflows
- The Action Centre creates powerful automation that fixes security issues as they're discovered, integrating with your existing tools through Power Automate, ServiceNow, and Jira.
- Custom Risk Intelligence
- The Logic Engine enables sophisticated risk profiling and automated data transformations aligned to your specific compliance frameworks and security policies.
- Visualise Environment Mapping
- The Device Explorer provides an intuitive globe view of your entire IT estate, instantly identifying high-risk devices and their connections to critical business applications.
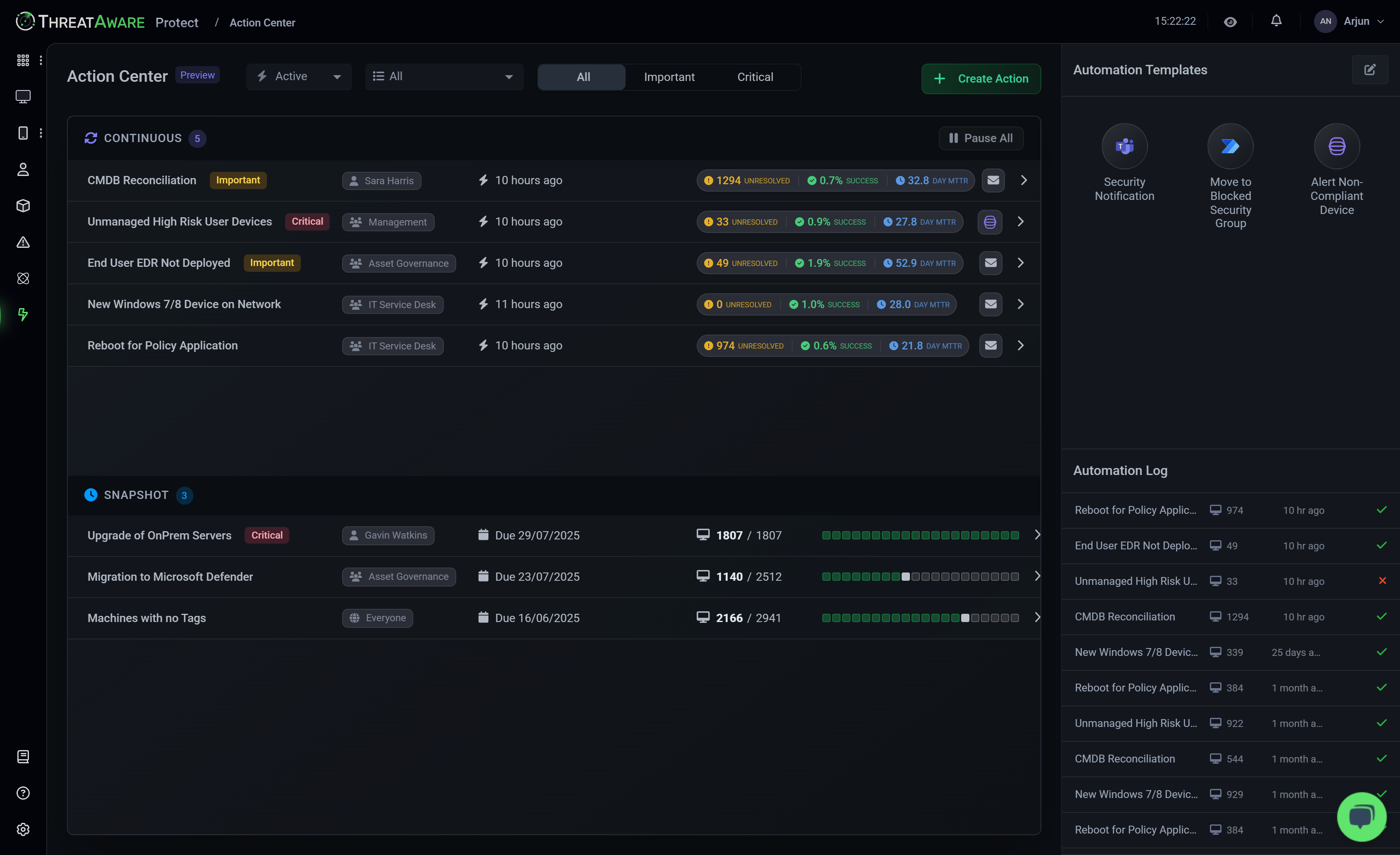
Achieve superior Cyber Hygiene with ThreatAware Protect, ensuring all security controls are operational.
Secure Every Device in Your Network
Instantly uncover and protect every asset in your IT estate with ThreatAware.
Identify unknown devices, reconcile asset data across platforms, and eliminate security gaps to ensure continuous cyber hygiene.
Book a Demo