The Technology
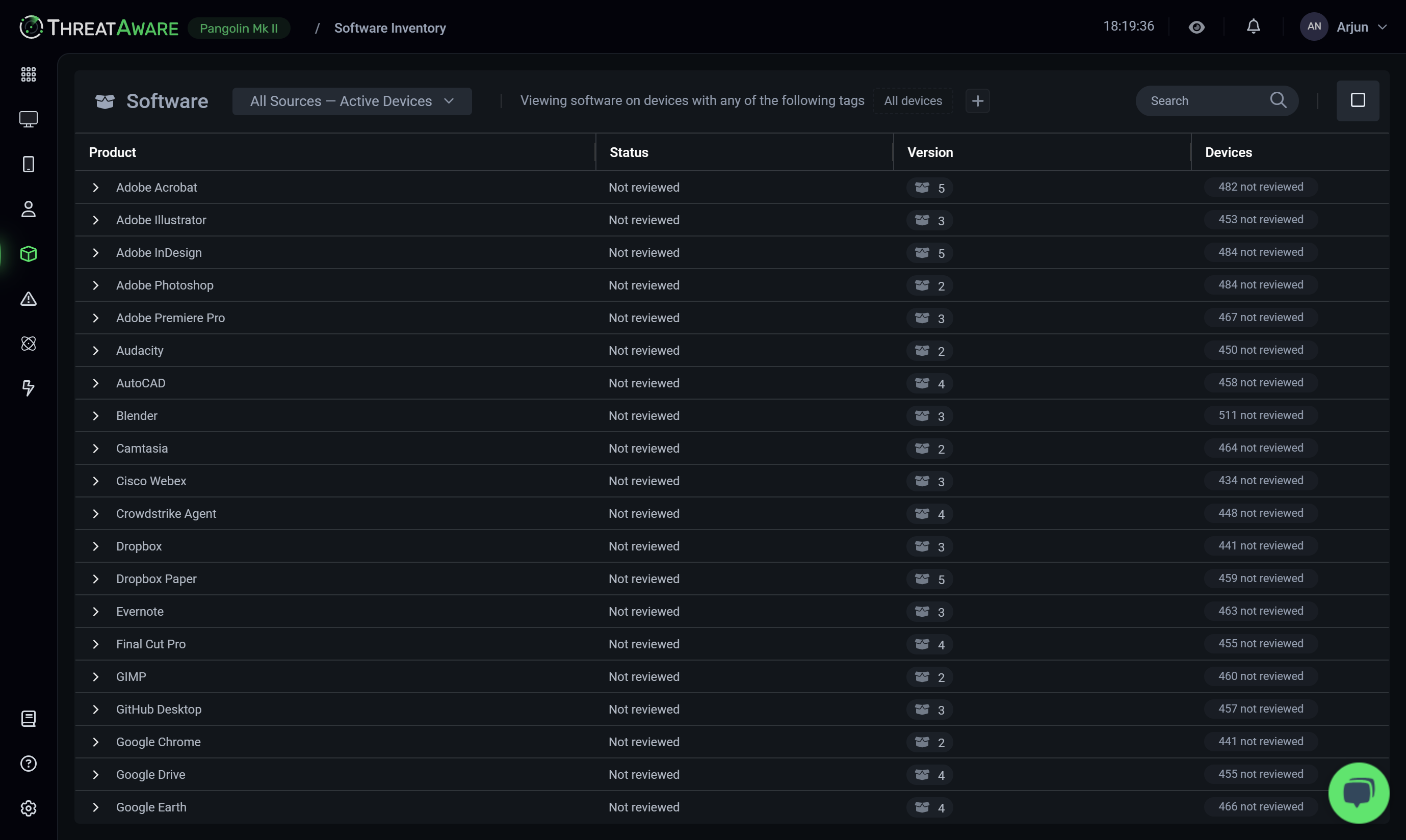
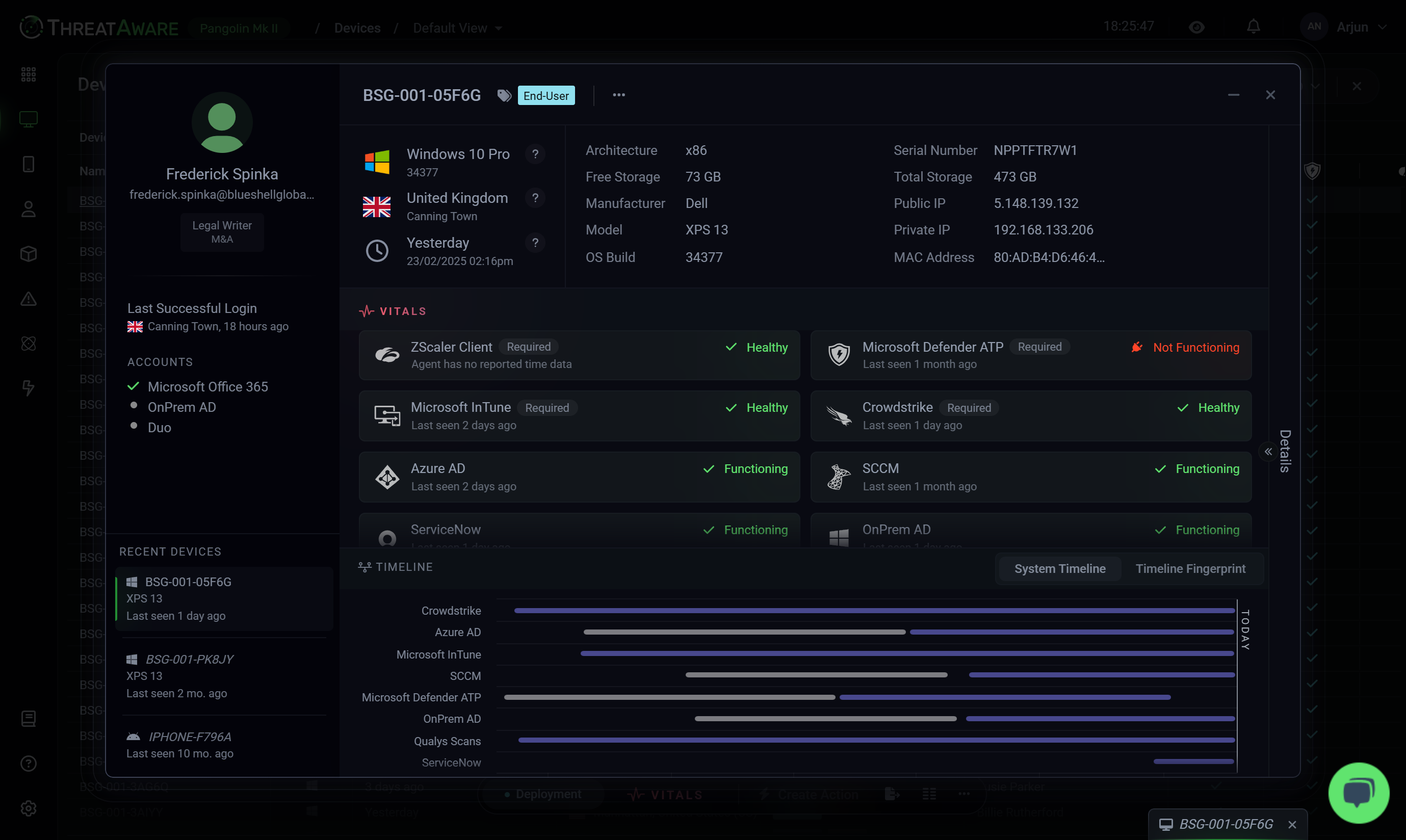
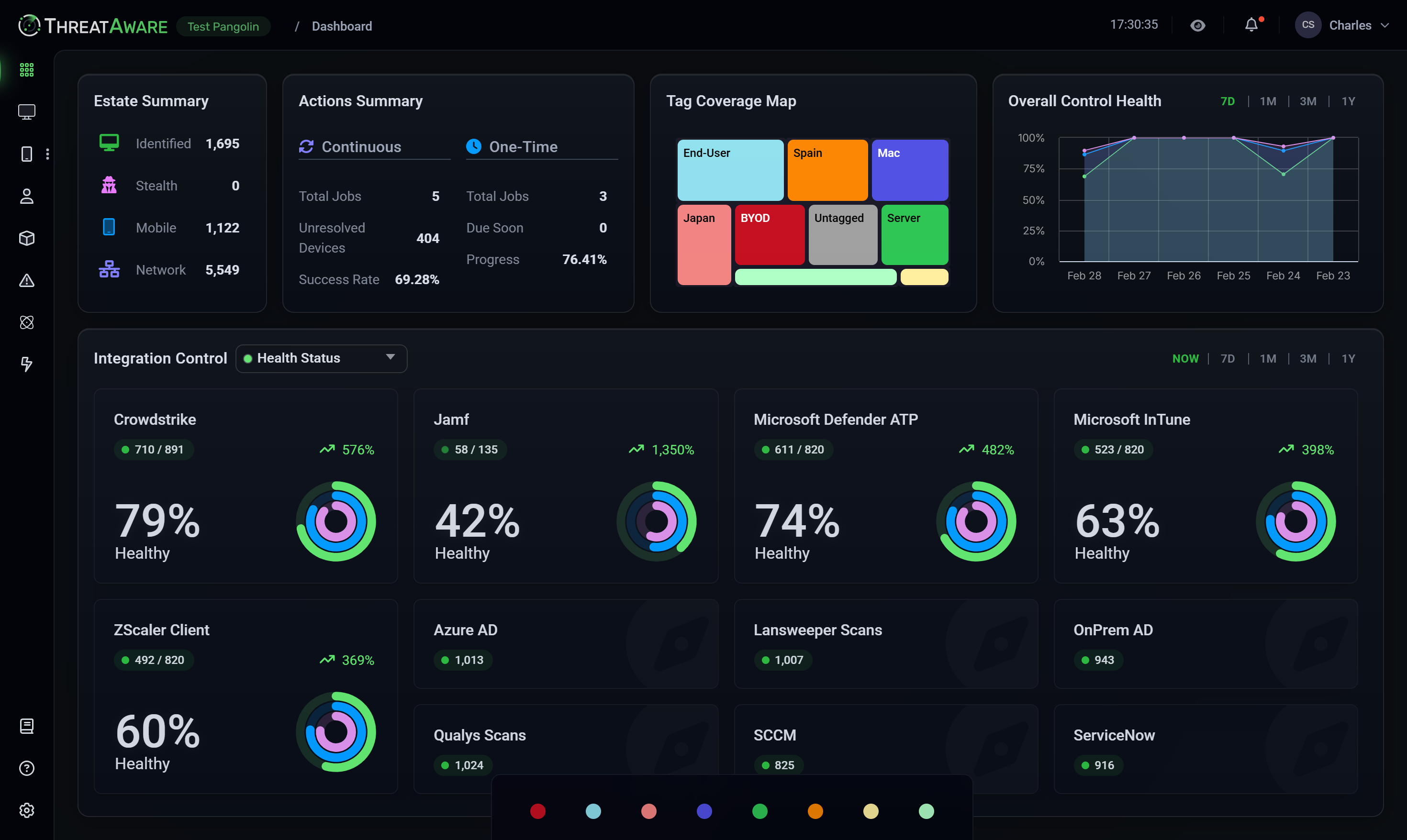
Total Cyber Asset Clarity
Eliminate blind spots and take full control with ThreatAware. Our agentless platform continuously uncovers hidden assets, validates security controls, and ensures every device remains protected—automatically, in real time.

ServiceNow
Management URL
https://api.us.servicenow.com
API Key
••••••••••••••••••

Intune
Management URL
https://graph.microsoft.com
API Key
••••••••••••••••••

Zscaler
Management URL
https://admin.zscaler.net
API Key
••••••••••••••••••

Tenable
Base URL
https://api.tenable.com
ClientID
blueshellglobal
API Key
••••••••••••••••••

GET
/api/v1/hosts



Device ID
"device_id":"D2001",
D2001
Hostname
"device_name":"BSG-0001-A2",
BSG-0001-A2
Last Seen
"last_login":"2025-01-15T14:22:00",
15/01/25 14:22 UTC
Status
"status":"0",
Online
Firmware Version
"firmware_vers":"v2.15",
v2.15
IP Address
"ip_address":"10.0.0.1"
10.0.0.1

Device ID
D3002
Hostname
BSG-0002-B1
Last Seen
22/01/25 09:45 UTC
Status
Offline
Firmware Version
v1.10
IP Address
192.168.10.24

Device ID
D1003
Hostname
BSG-0003-C3
Last Seen
20/01/25 16:00 UTC
Status
Online
Firmware Version
v3.01
IP Address
172.16.0.8

Device ID
D4004
Hostname
BSG-0004-D4
Last Seen
10/01/25 08:30 UTC
Status
Offline
Firmware Version
v4.20
IP Address
10.0.5.12

Device ID
D5005
Hostname
BSG-0005-E2
Last Seen
21/01/25 12:15 UTC
Status
Online
Firmware Version
v5.00
IP Address
192.168.1.200





10:00
12:00
13:00
14:00
15:00
16:00
17:00
Matching...
Matching complete
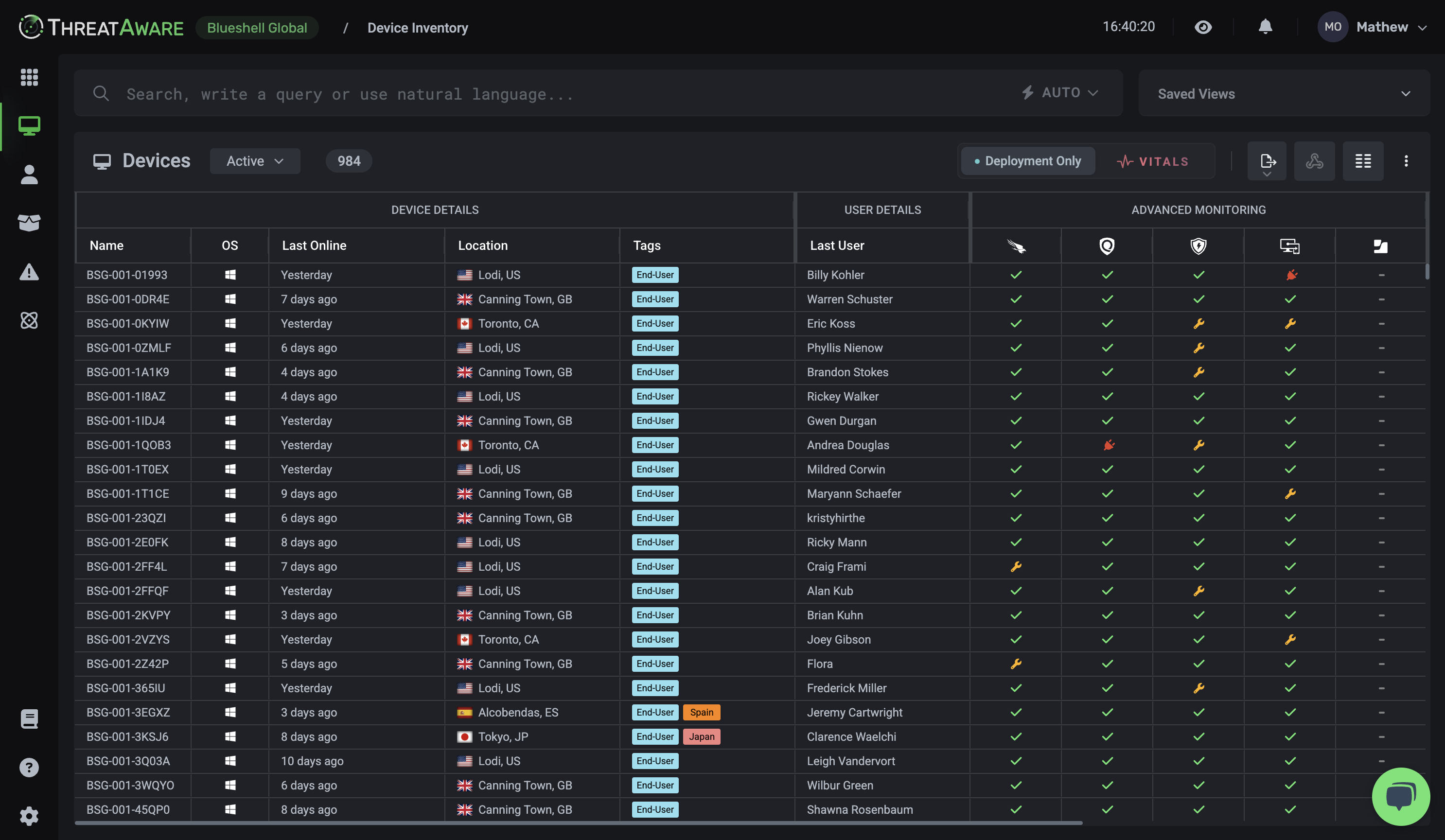



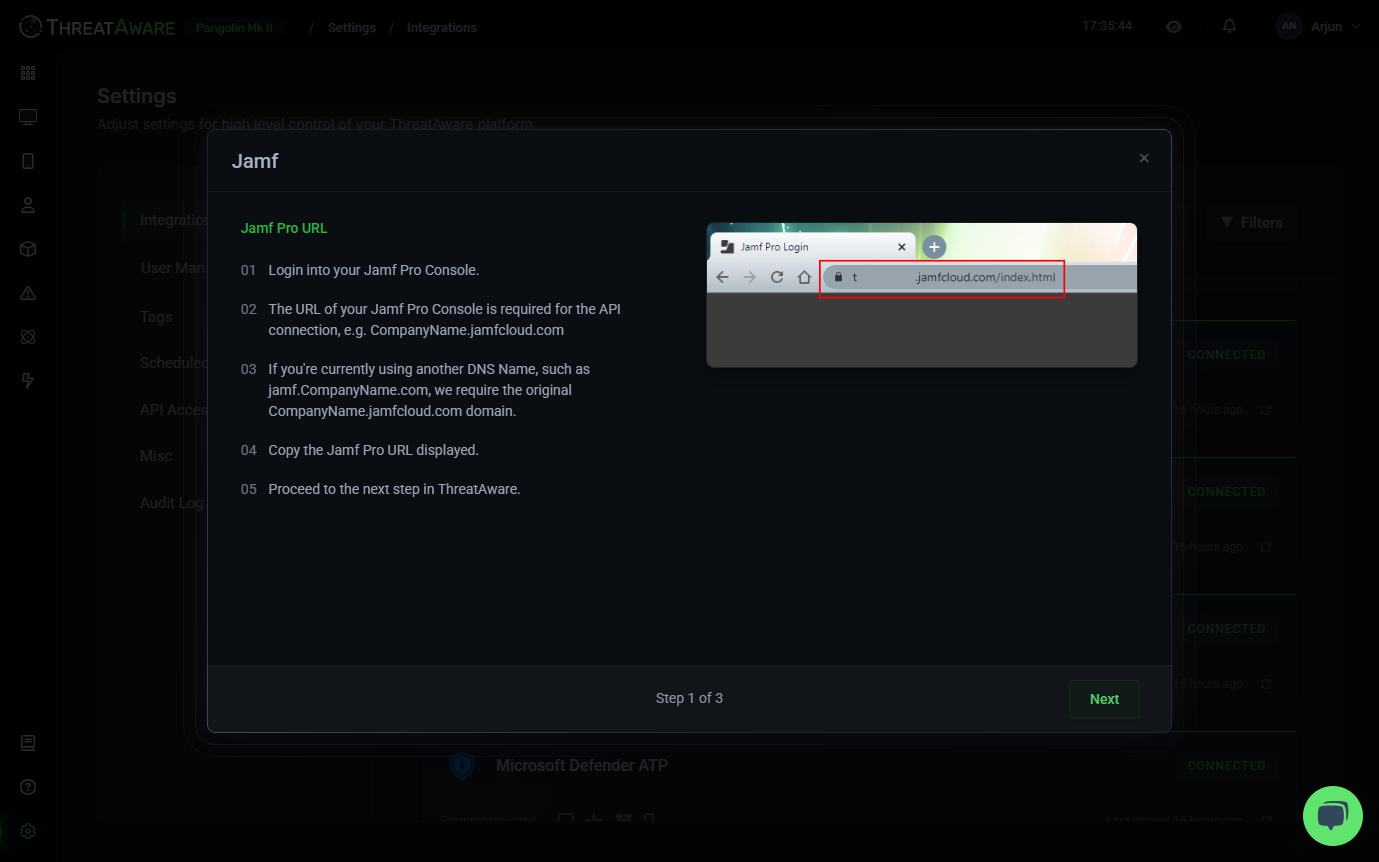
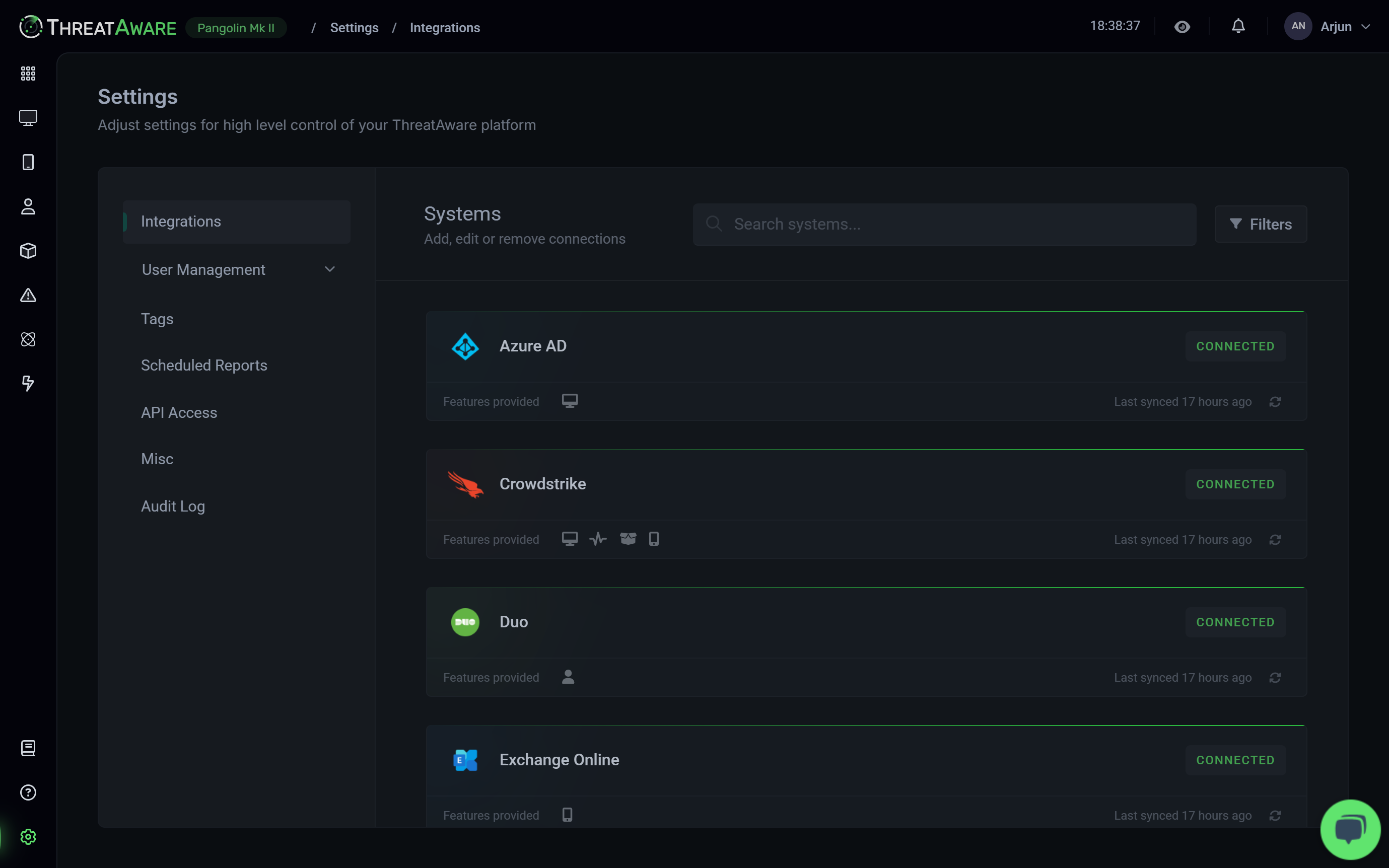
API Integration
Intelligent Data Correlation
Data Normalisation
Timeline Matching
Unified Monitoring and Insights
Platform Features
Comprehensive Security Management
API Integrations
Connect with hundreds of security and IT tools through our agentless platform. Our API-first approach enables seamless integration with your existing security stack, providing unified visibility and control.