Find & Fix Every Security Gap Across All Your Devices
ThreatAware gives you real-time visibility and continuously validates your security controls - so nothing slips through the cracks.

Trusted by Leading Organisations
Our clients come from all industries — from legal to finance, energy to retail. We are trusted by leading organisations to discover and protect their valuable cyber assets.




Cyber Resilience
Complete Visibility. Continuous Protection.
Security teams invest in tools, but too often, those tools operate in silos. Misconfigurations and blind spots leave around 15% of devices with gaps in protection.
ThreatAware unifies your entire security stack, uncovers hidden assets, and automates remediation, so every device is protected, and your tools work together as one.
No More Gaps.
Take Control of Your Entire IT Estate
ThreatAware gives you full visibility of every device and control, protecting your IT estate in real time.
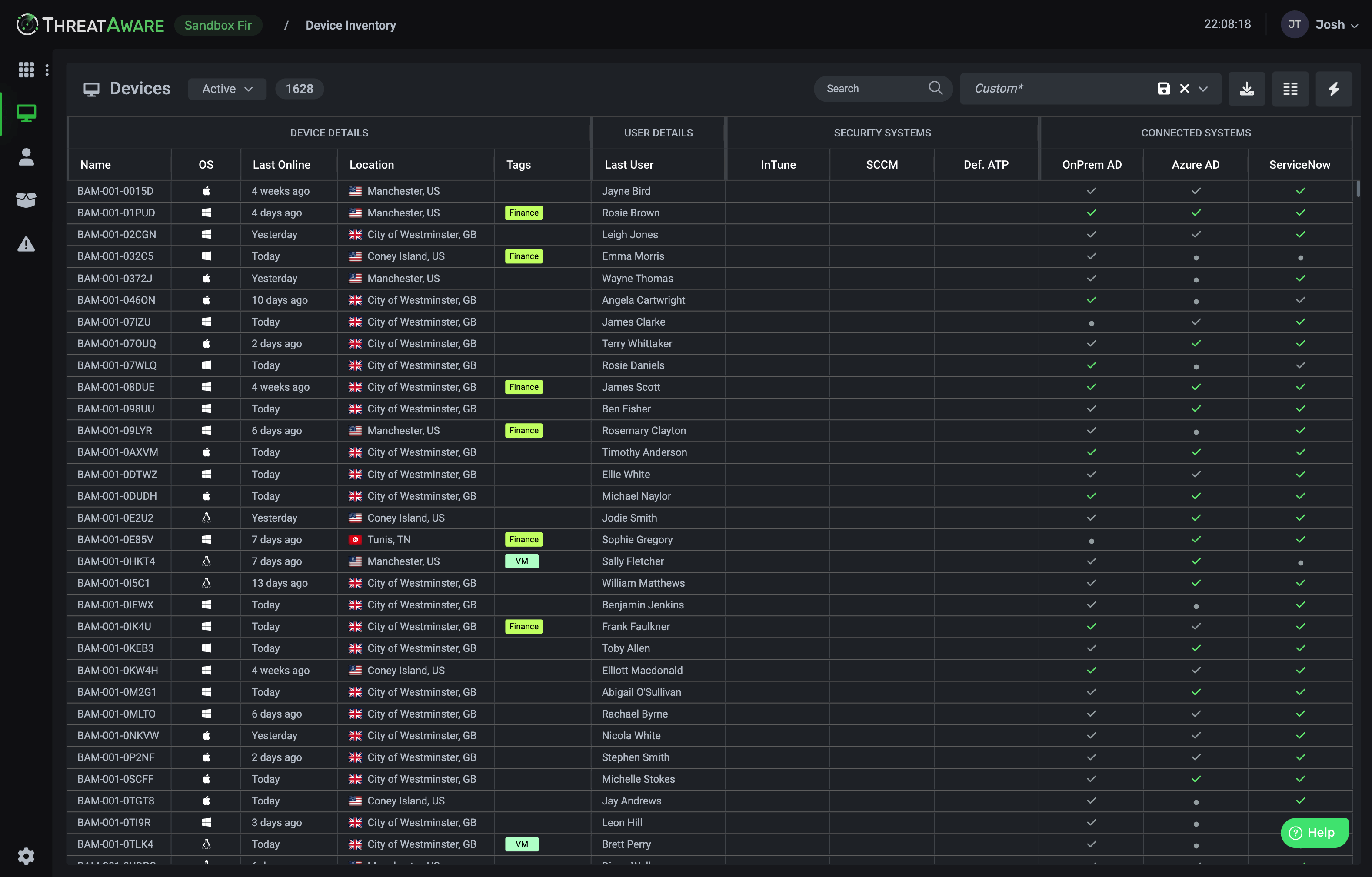
- See Everything, Miss Nothing
- Automatically discover every device and installed application, with timeline-matching technology that eliminates duplicates.
- Fix Security Gaps Before They're Exploited
- Instantly detect missing or broken controls like EDR, MFA, or encryption.
- Automate the Manual Work
- Cut down repetitive tasks with workflows, alerts, and automated reporting — so your team can focus on action, not admin.
- Streamline Asset Management
- Intelligently tag and organise assets by risk, compliance, or business unit. Easily prioritise what matters, with a fully customisable visual editor.
- Accelerate Incident Investigation
- Get to the root cause faster with powerful search and deep device-level insights using our unique X-Ray view.
- Stay Audit-Ready Always
- Maintain compliance with customisable dashboards, automated reports, and complete visibility across every part of your environment.

We have over 50,000 devices made up of desktops, laptops, servers and virtual machines. The biggest win from using ThreatAware is actually having confidence in all the assets we have and what security we have on them.

































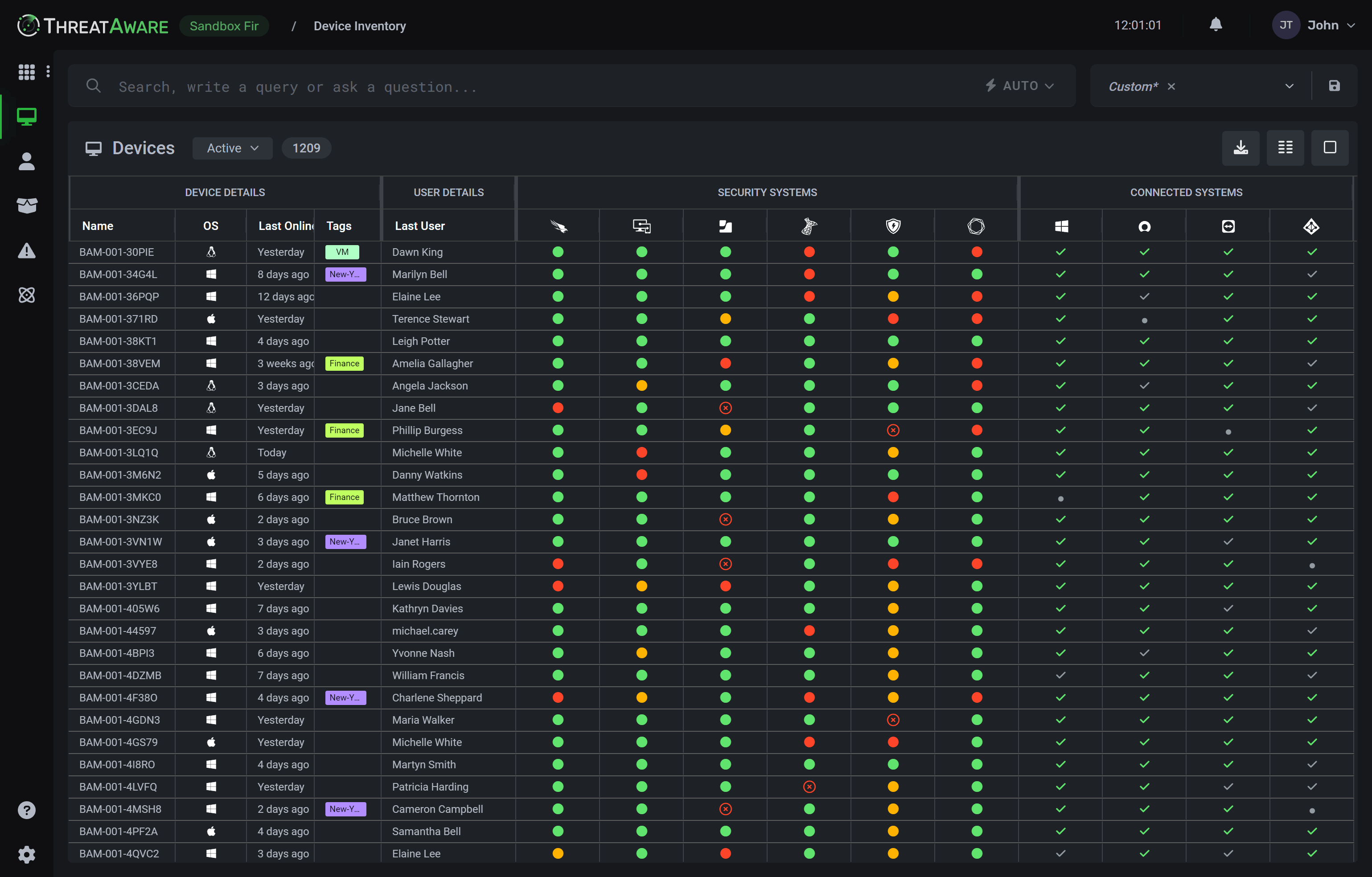
Integrations
Your Tools Connect to ThreatAware
ThreatAware integrates with your security tools through simple API connections in under 30 minutes, transforming disconnected data into unified, actionable intelligence.
Explore our integrations →Cyber Intelligence
Cyber Asset Attack Surface Management. Transformed.
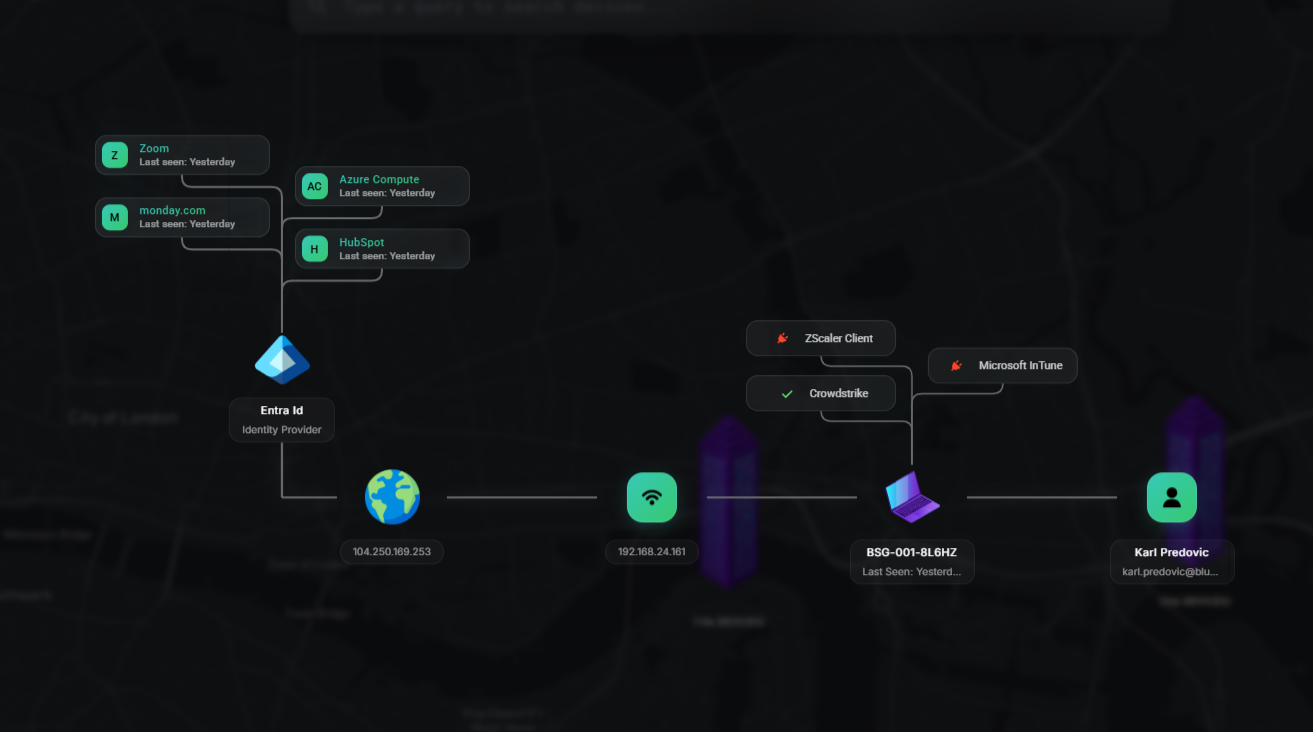
ThreatAware redefines CAASM with unmatched accuracy powered by proprietary timeline-matching technology, transforming how organisations validate and protect every device across their IT estate.
- A Single Source of Truth
- Reveal every device, no duplicates, no blind spots. ThreatAware delivers complete visibility and continuously validates security controls across your environment.
- Proprietary Timeline-Matching Algorithm
- Our patent-pending technology builds unique fingerprints for each device based on behavioural patterns, uncovering hidden “stealth” devices that other tools miss.
- From Detection to Resolution
- Insight alone isn't enough. ThreatAware's Action Centre automates remediation, closes security gaps, and enforces policies across every device, at speed and scale.
Customer Stories
See how the world's most innovative organisations use ThreatAware to manage vast and complex IT environments.

“The biggest win from using ThreatAware is actually having confidence in all the assets we have and what security we have on them.”

Douglas Weekes
CISO, Sainsbury's

“The cyber posture of the business doesn't stand still and ThreatAware is a single source of truth.”

Lyndon Arnold
Head of IT, BGF

“ThreatAware's ability to automate and centralise asset management has been pivotal in enhancing our cybersecurity resilience, allowing the team to focus on strategic initiatives.”

Abraham Ingersoll
Chief Security Officer, THG
Blogs
Check out the latest news about ThreatAware and the cyber security industry.
Secure Every Device in Your Network
Instantly uncover and protect every asset in your IT estate with ThreatAware.
Identify unknown devices, reconcile asset data across platforms, and eliminate security gaps to ensure continuous cyber hygiene.
Book a Demo



