ThreatAware Connect
Comprehensive Asset Visibility
Gain complete visibility of every device in your corporate environment and establish your security foundation.




What Connect Offers
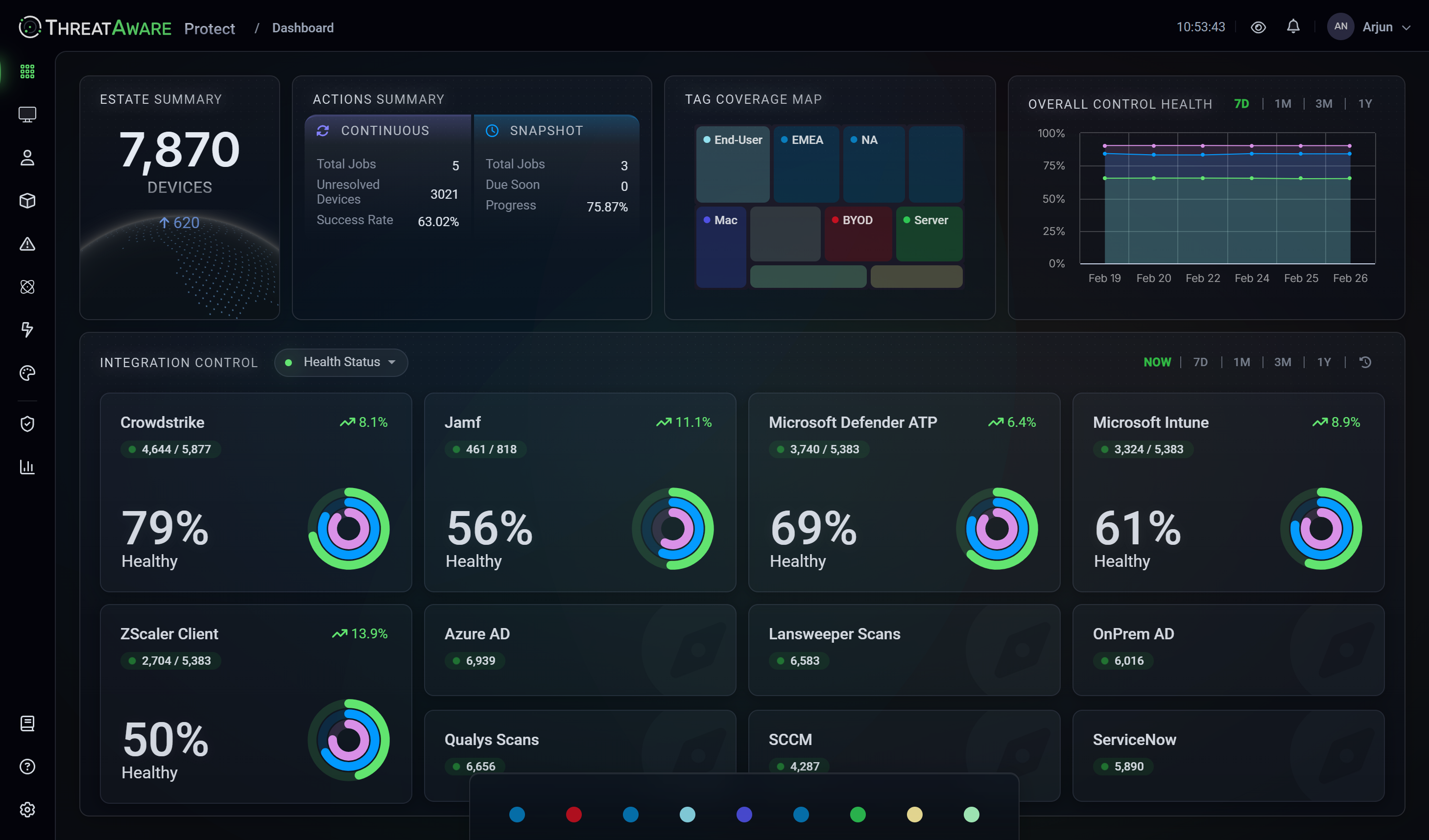
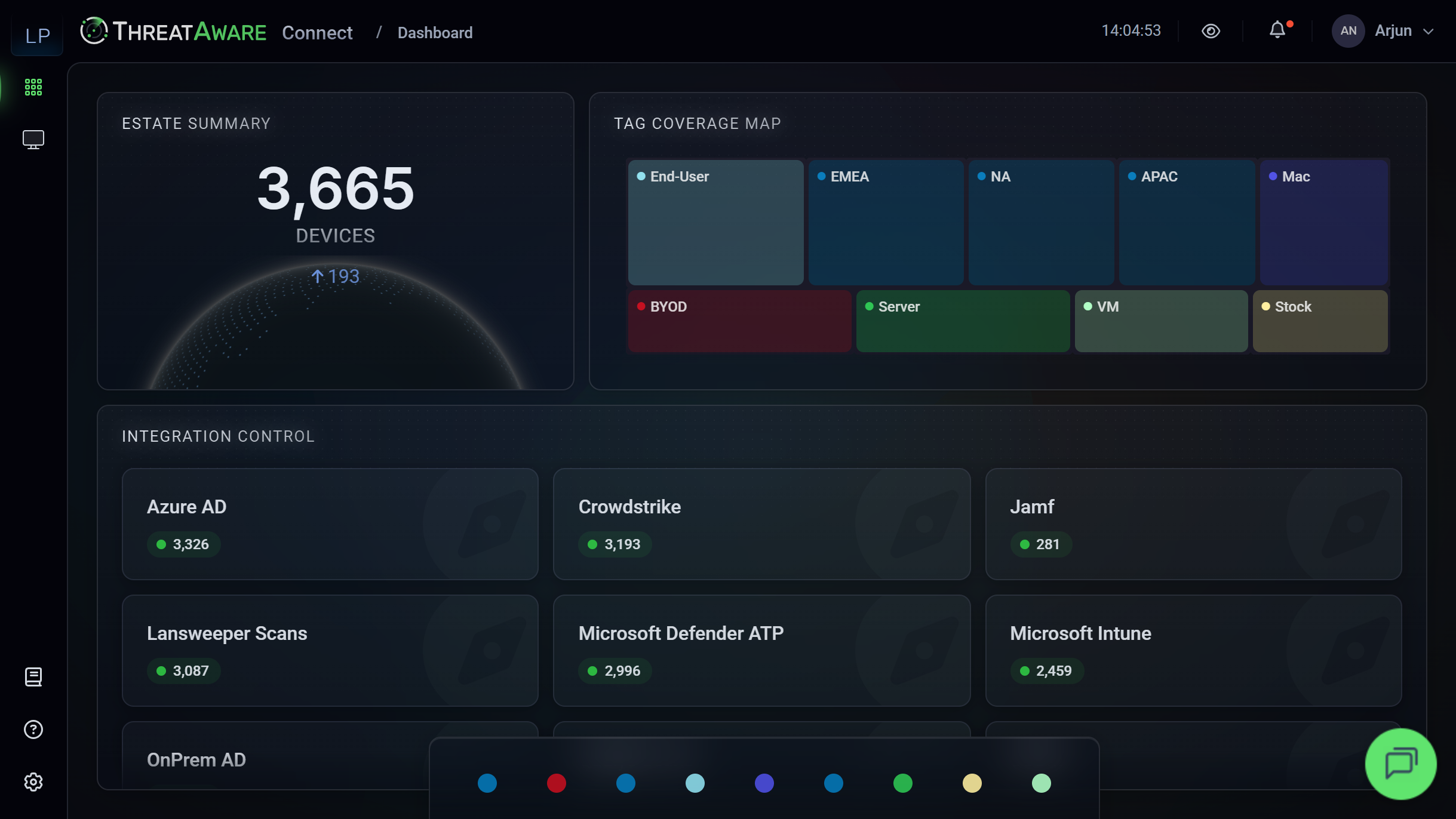
Connect gives you the foundation of visibility by showing every device in your environment and whether your security agents are deployed. It discovers managed devices, unmanaged devices, and shadow IT so you have a complete and accurate view of your IT estate. Connect provides a single source of truth with clear awareness of coverage gaps, forming the baseline you need before validation or automation.
Find every device accessing your corporate environment with complete visibility.
Full deployment visibility, plus see which devices have security agents deployed, functioning and configured correctly.
Complete platform access, plus automated workflows and AI-powered custom dashboards for proactive defence.
Connect
Find every device accessing your corporate environment with complete visibility.
Discover
Full deployment visibility, plus see which devices have security agents deployed, functioning and configured correctly.
Protect
Complete platform access, plus automated workflows and AI-powered custom dashboards for proactive defence.
Timeline Matching Technology
Discover 20-30% more assets than conventional methods
Device Discovery
Our timeline matching algorithm creates unique device fingerprints by analysing activity patterns across all connected tools.
This discovers devices that traditional methods miss whilst eliminating duplicate records.
- Timeline Matching: Correlates devices across tools by behaviour patterns, not just identifiers. Finds devices other platforms miss.
- Deduplication: Intelligent matching eliminates duplicates. One device, one record, regardless of how many tools see it.
- Complete Visibility: See every device - desktops, laptops, servers, mobile devices, virtual machines - in a single view.
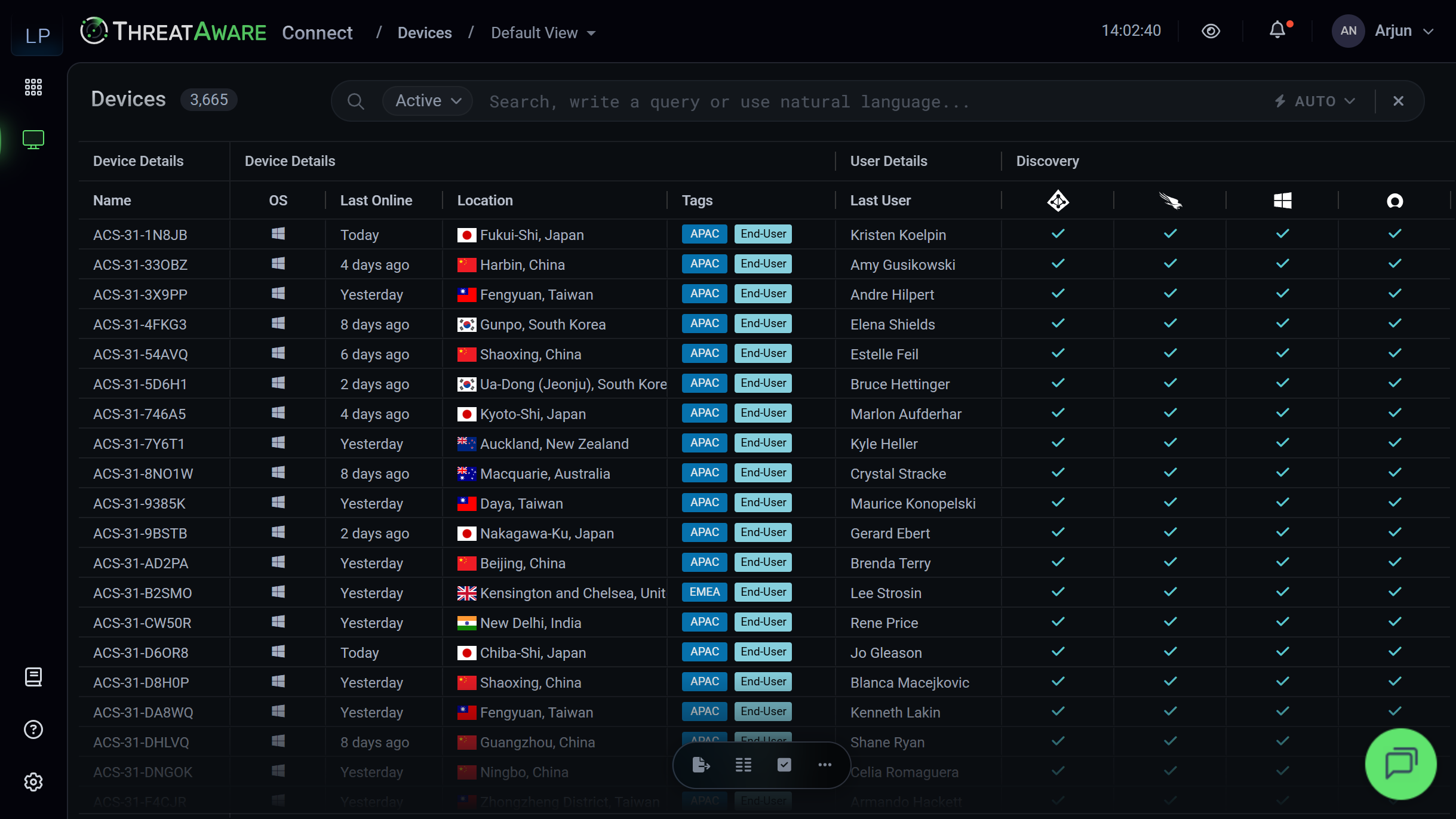
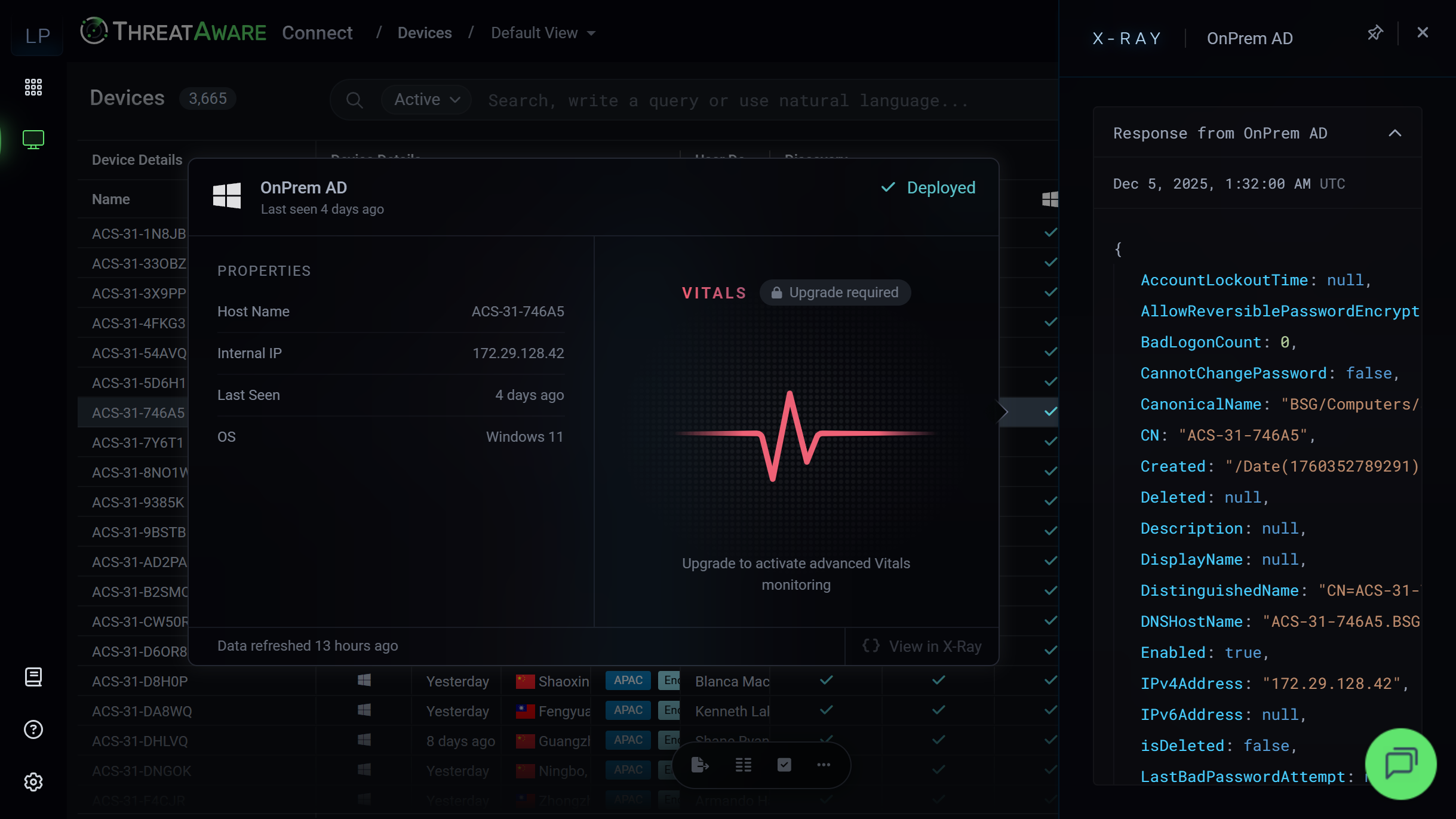
Agent Deployment Detection
Once devices are discovered, Connect shows you which security agents are deployed on each device.
Know immediately where you have coverage and where you have gaps.
- EDR Coverage: See which devices have endpoint detection and response agents deployed.
- MDM Enrolment: Identify devices enrolled in mobile device management.
- Security Stack Visibility: Track deployment of encryption, antivirus, backup agents and more.
Agentless & Continuous by Design
Real-time visibility without deployment overhead
Agentless Design
Connect to your existing tools through simple API integrations. No agents to deploy, maintain or troubleshoot.
- API connections to 200+ security and IT tools
- Read-only access, no risk to your environment
- 2-5 minute setup per integration
- On-premise connector for internal tools
- Zero performance impact on endpoints
Continuous Monitoring
Your asset inventory updates automatically every 60 minutes. Stay current as devices join, leave and change.
- Hourly automatic refresh across all integrations
- On-demand updates when you need them
- Real-time notifications for new devices
- Historical tracking for compliance
- Trend analysis over time
Connect into All Your Tools
200+ integrations across your security stack
Need More Than Deployment Status?
Connect reveals deployment status across your estate. Discover goes deeper - validating that agents are functioning and properly configured, not just installed.
Secure Every Device in Your Network
Instantly uncover and protect every asset in your IT estate with ThreatAware.
Identify unknown devices, reconcile asset data across platforms, and eliminate security gaps to ensure continuous cyber hygiene.
Book a Demo