ThreatAware Discover
Security Control Validation
Validate that security agents are not just deployed, but functioning correctly and properly configured across your environment.




What Discover Offers
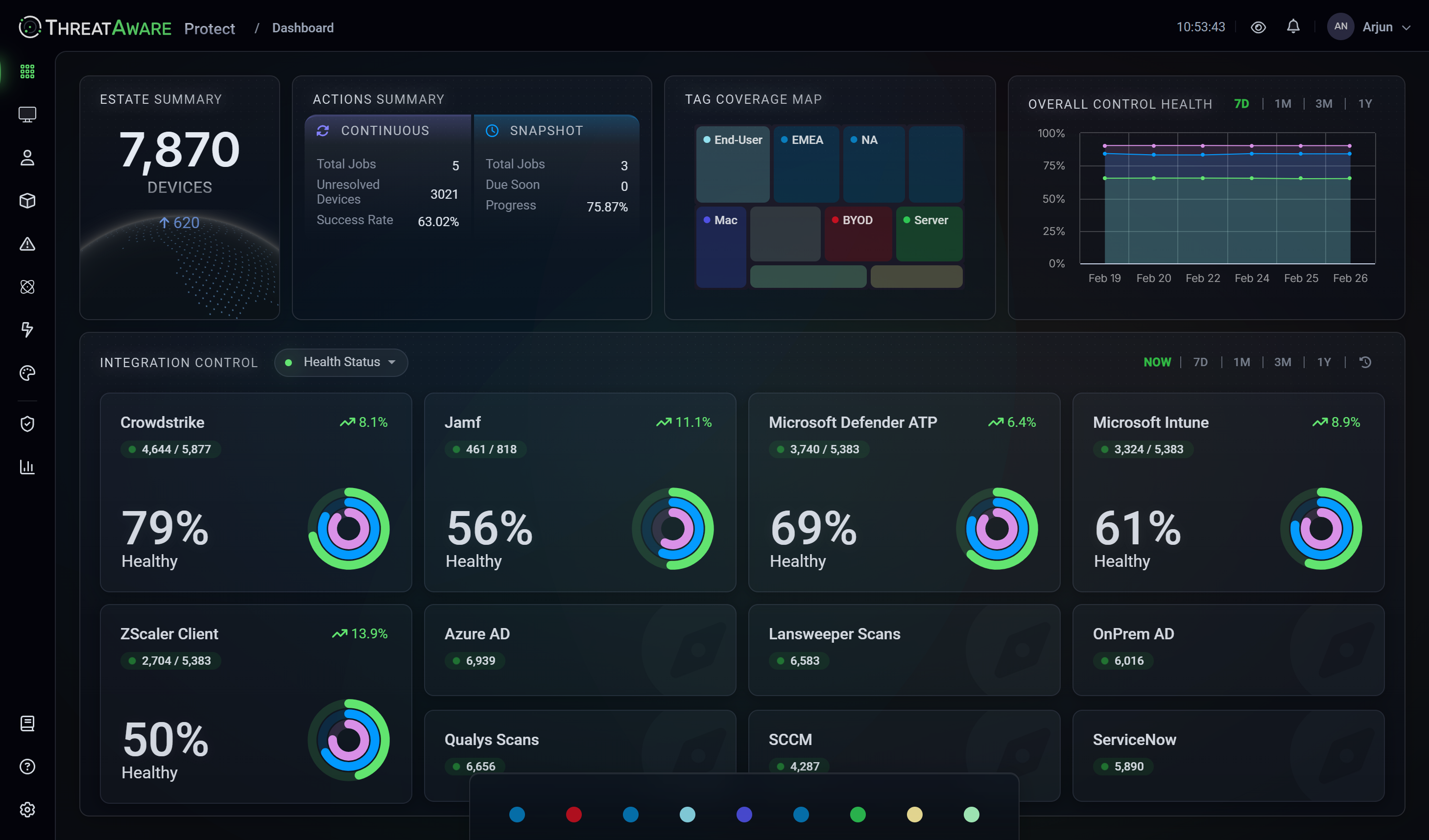
Discover proves your security controls are working, not just installed. It discovers every device across your environment, shows deployment status, and then validates that agents are active, correctly configured, and enforcing policy. Discover exposes silent failures where tools appear healthy but are not protecting devices. This allows you to fix issues before they become security incidents.
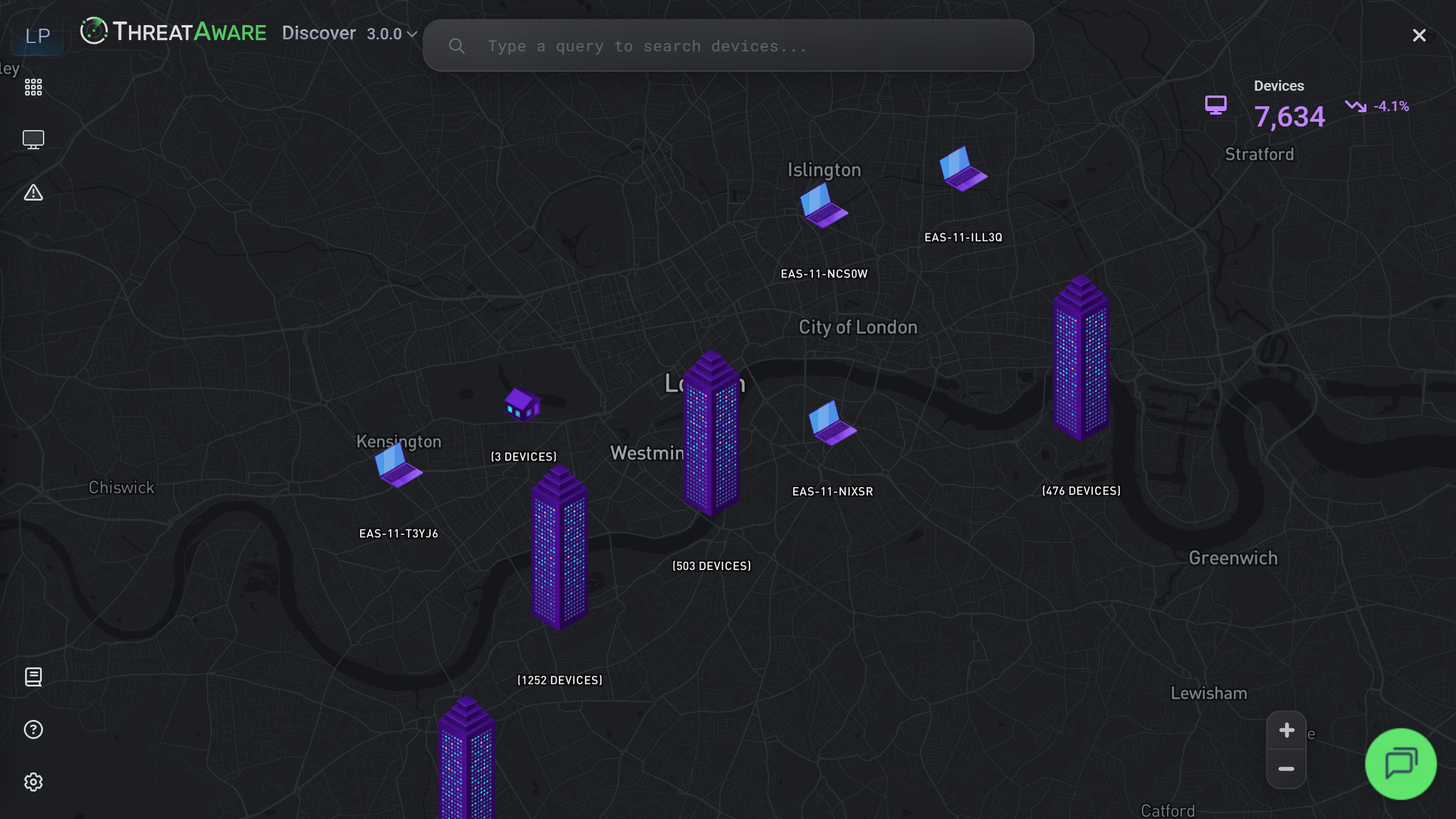
Find every device accessing your corporate environment with complete visibility.
Full deployment visibility, plus see which devices have security agents deployed, functioning and configured correctly.
Complete platform access, plus automated workflows and AI-powered custom dashboards for proactive defence.
Connect
Find every device accessing your corporate environment with complete visibility.
Discover
Full deployment visibility, plus see which devices have security agents deployed, functioning and configured correctly.
Protect
Complete platform access, plus automated workflows and AI-powered custom dashboards for proactive defence.
Control Validation
Deployed, functioning and configured - complete confidence
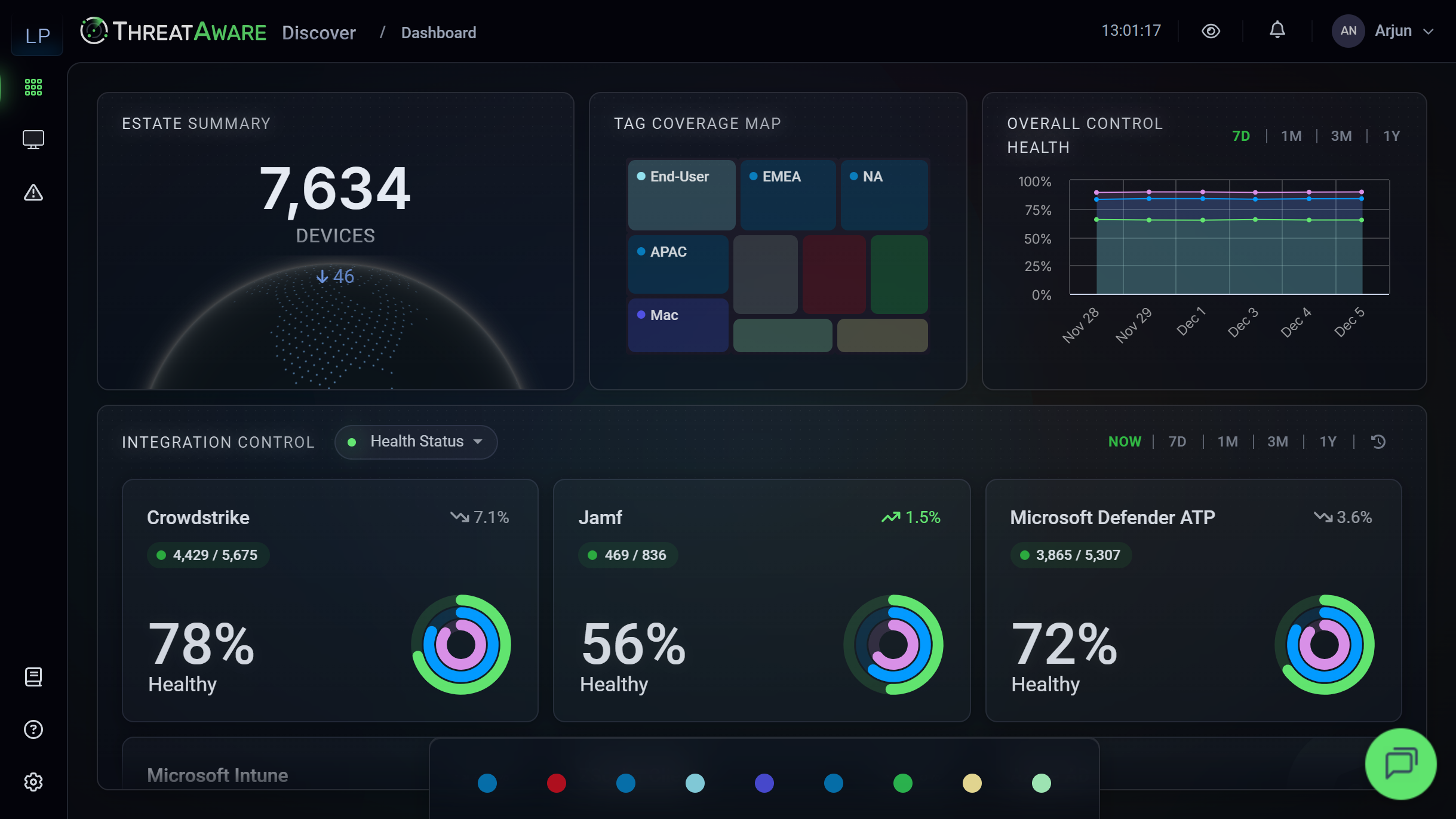
Control Agent Functioning
An agent showing as "deployed" doesn't mean it's working.
Discover validates that agents are actively functioning and reporting, not just installed.
- Active Communication: Verify agents are reporting back to their management console, not just sitting idle.
- Cross-Platform Correlation: Catch silent failures, when an agent appears healthy in its console but isn't actually protecting the device.
- Real-Time Status: Hourly validation ensures you catch problems within 60 minutes, not days or weeks.
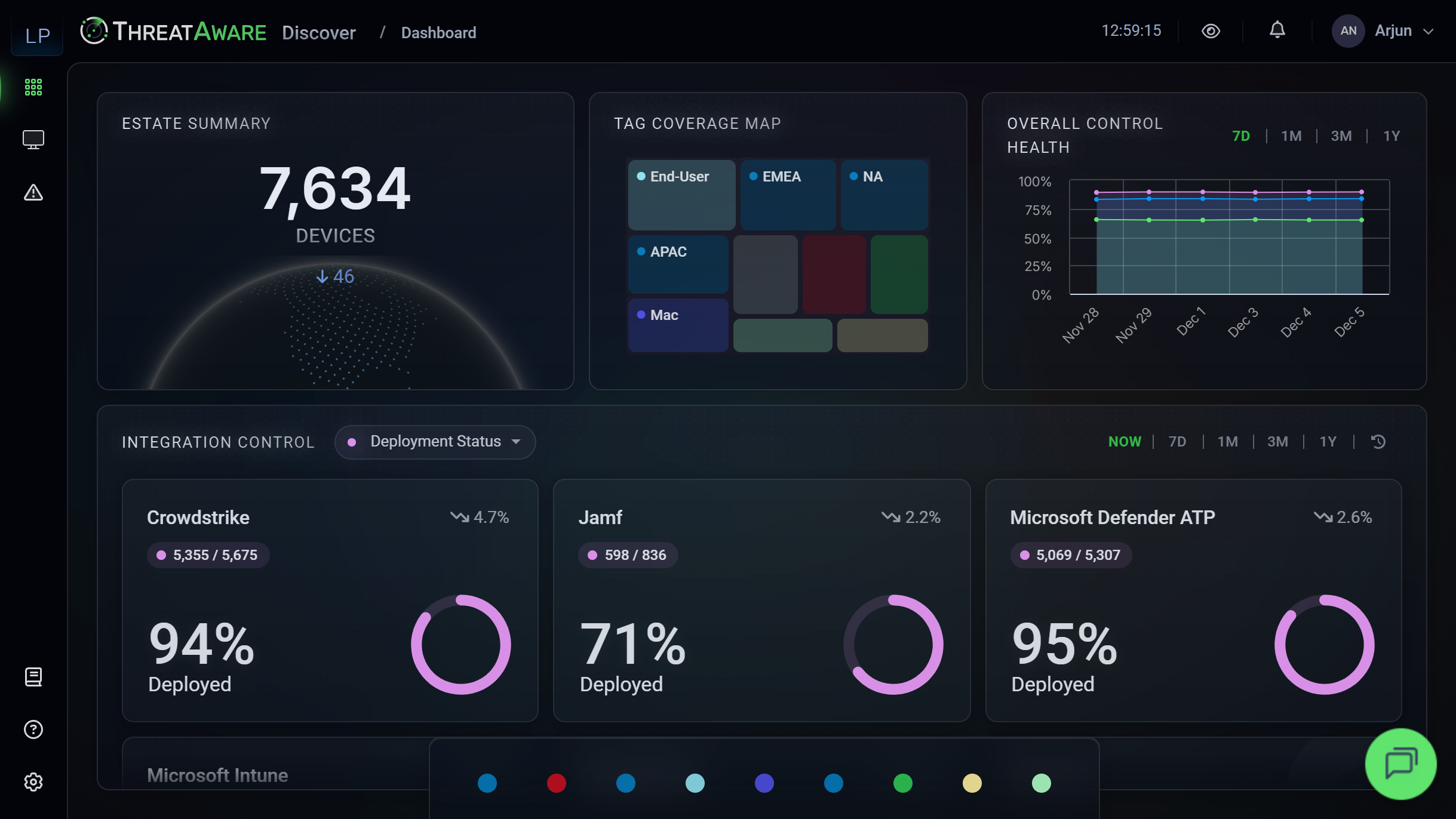
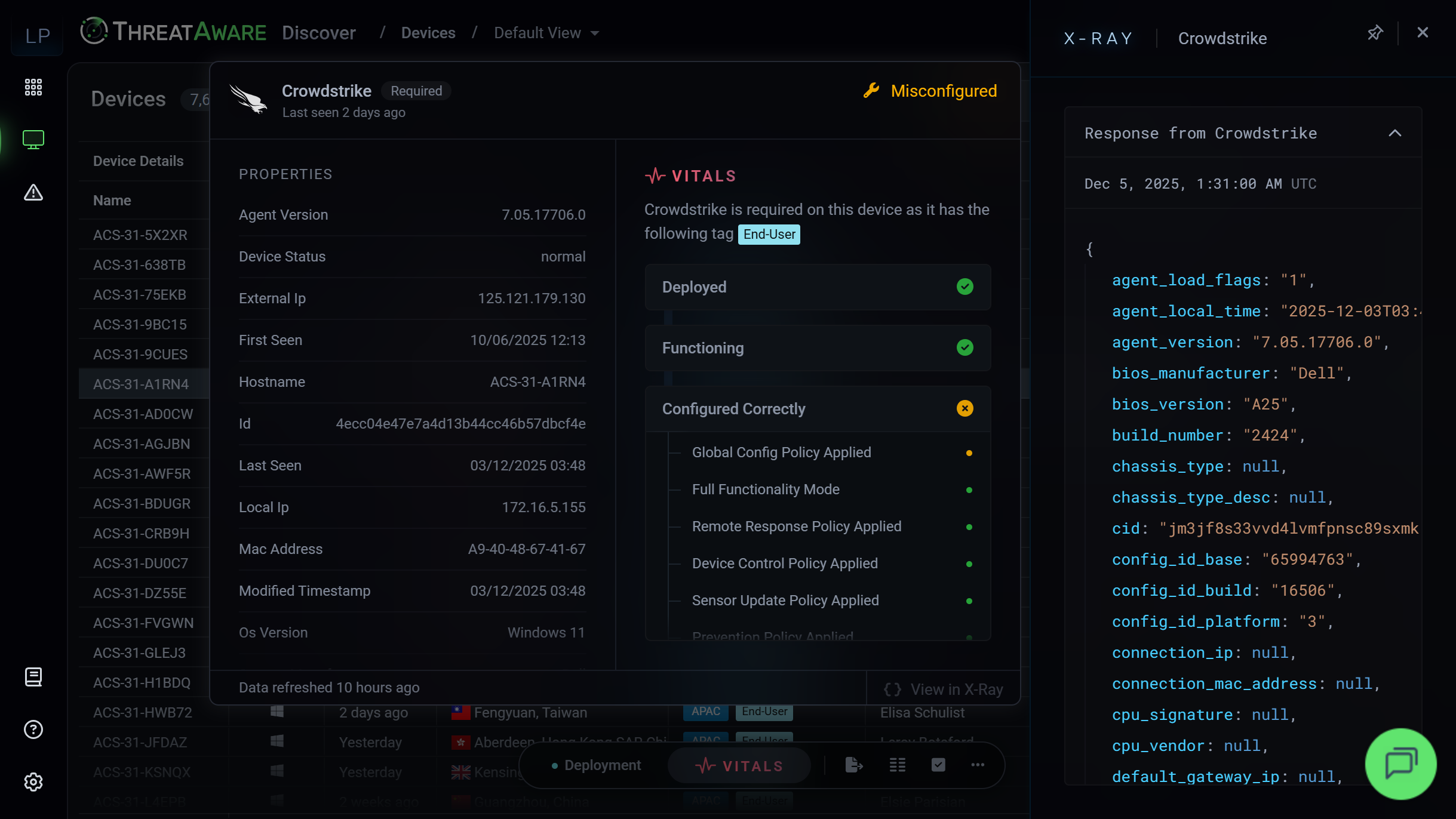
Configuration Monitoring
A functioning agent with the wrong configuration leaves you exposed.
Discover validates that agents are configured correctly with proper policies applied.
- Policy Validation: Ensure security policies are applied correctly, not using default or outdated configurations.
- Configuration Drift: Detect when agents drift from your standard configuration and alert immediately.
- Compliance Tracking: Track configuration compliance across your entire estate for audit and governance.
Logic Engine: Organise Your Data Your Way
Create custom fields and data transformations built around your business logic.
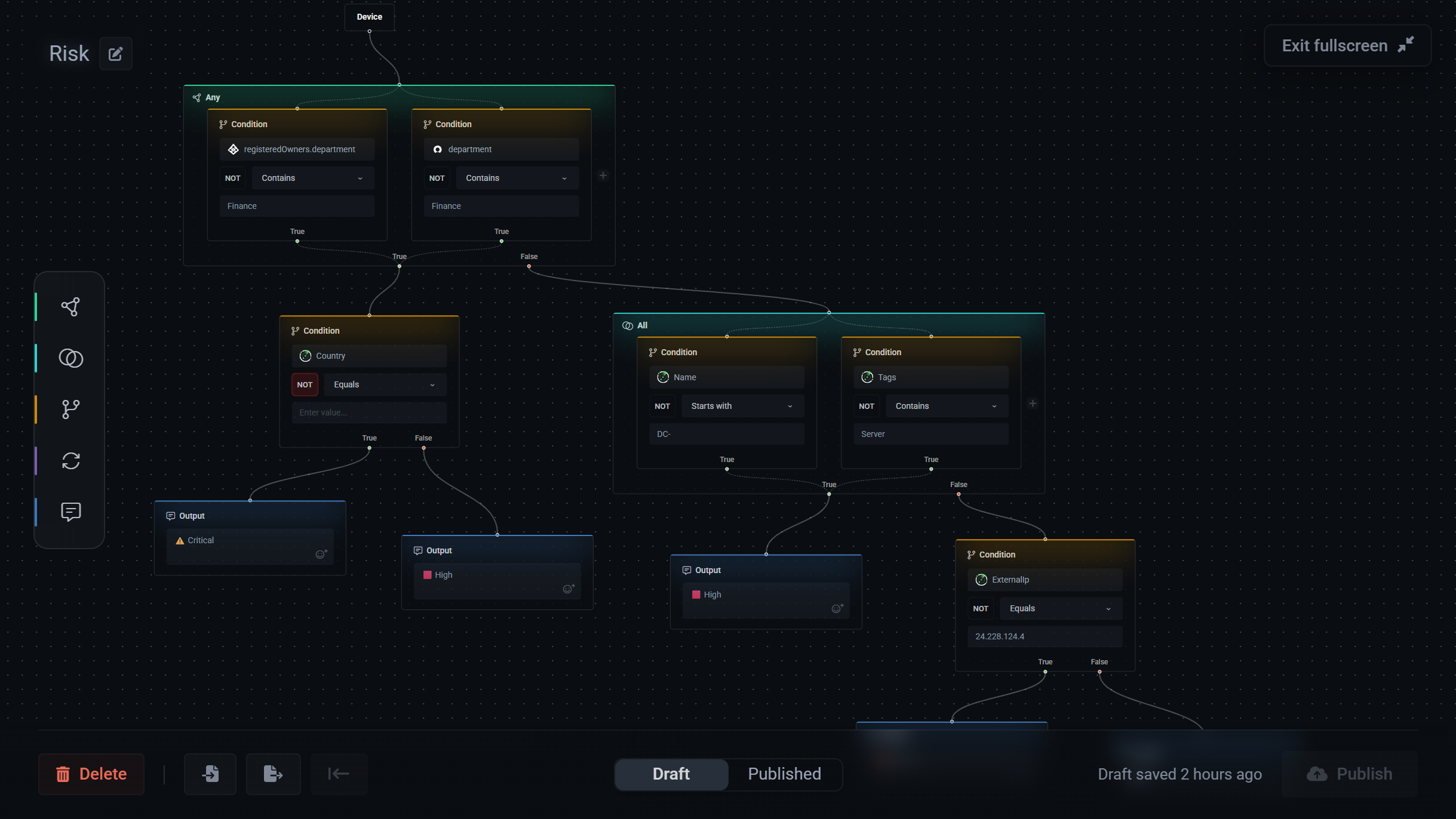
Custom Risk Scoring
Create risk scores based on your factors, device type, user role, data access, control status. Weighted for your business.
Compliance Mapping
Map your data to compliance frameworks: ISO 27001, NIST CSF, Cyber Essentials. Automate your evidence collection.
Business Context
Enrich device data with business context: department, location, criticality, owner. Organise by what matters to you.
Built on Connect's Foundation
All of Connect's capabilities, plus advanced validation
Timeline Matching & Discovery
Device discovery technology finds 20% more assets than conventional methods.
- Complete device visibility across all tools
- Intelligent deduplication
- Global device mapping
- Active and inactive inventory
Agentless & Continuous
API integrations to 200+ tools with hourly automatic updates.
- No agents to deploy or maintain
- 60-minute update frequency
- Read-only security
- On-premise connector support
Need Automated Remediation?
Discover validates your controls and shows you gaps within your IT estate. Protect closes those gaps automatically, turning alerts into action.
Secure Every Device in Your Network
Instantly uncover and protect every asset in your IT estate with ThreatAware.
Identify unknown devices, reconcile asset data across platforms, and eliminate security gaps to ensure continuous cyber hygiene.
Book a Demo