ThreatAware Protect
Proactive Defence & Compliance
Reduce threats with complete visibility, trustworthy data, and remediation you can prove.




What Protect Offers
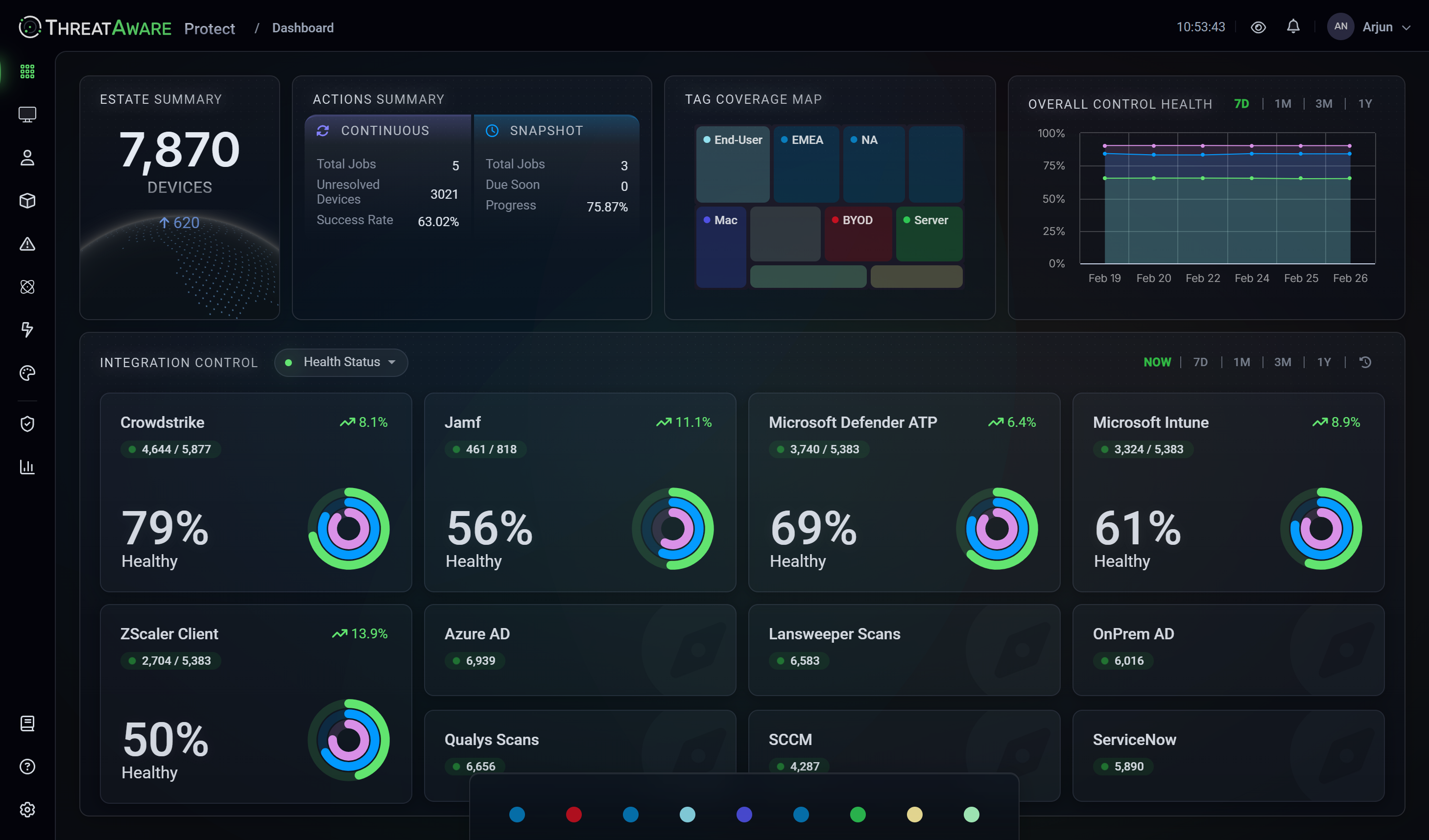
Protect goes beyond visibility and validation to ensure your security controls are always working. It shows you every device in your environment and reveals where agents are missing, broken or misconfigured – turning blind spots into actionable fixes. When gaps are found, Protect automates the entire response, creating tickets, alerting teams, triggering remediation and confirming resolution.
Find every device accessing your corporate environment with complete visibility.
Full deployment visibility, plus see which devices have security agents deployed, functioning and configured correctly.
Complete platform access, plus automated workflows and AI-powered custom dashboards for proactive defence.
Connect
Find every device accessing your corporate environment with complete visibility.
Discover
Full deployment visibility, plus see which devices have security agents deployed, functioning and configured correctly.
Protect
Complete platform access, plus automated workflows and AI-powered custom dashboards for proactive defence.
Complete Security Platform
Everything you need to protect your organisation
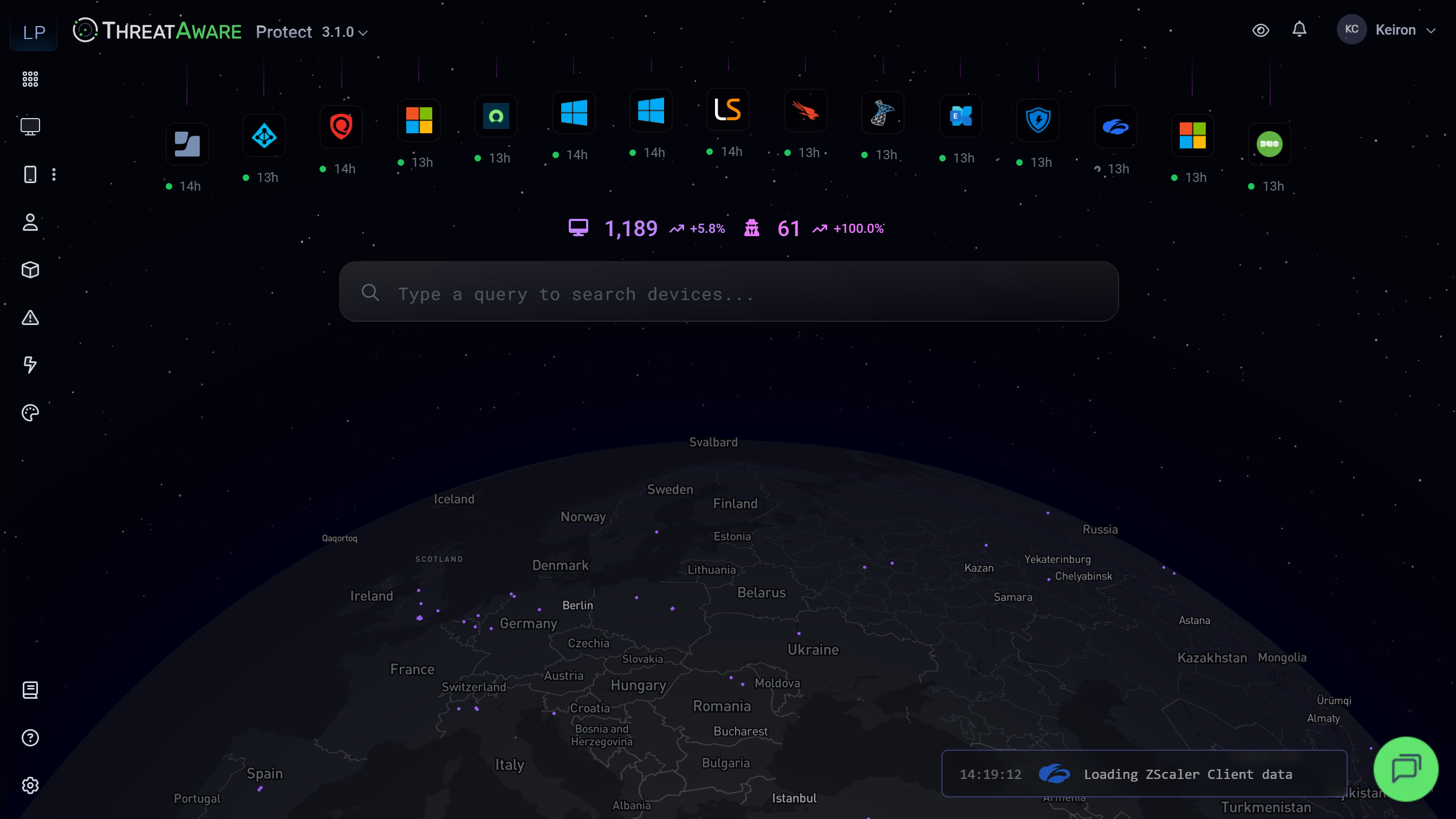
Advanced Discovery
Complete visibility across your entire IT estate with intelligent discovery.
- Stealth Device Detection: Discover devices that appear in one tool but are completely invisible in others. Identify significant security blind spots.
- Software Inventory: Complete visibility into installed applications. Identify shadow IT, track licence compliance and detect vulnerable software.
- User Inventory: Comprehensive user tracking. Monitor user access, device associations and security posture at the user level.
- Globe View: Interactive visualisation of your entire IT estate. Identify high-risk devices and geographical distribution instantly.
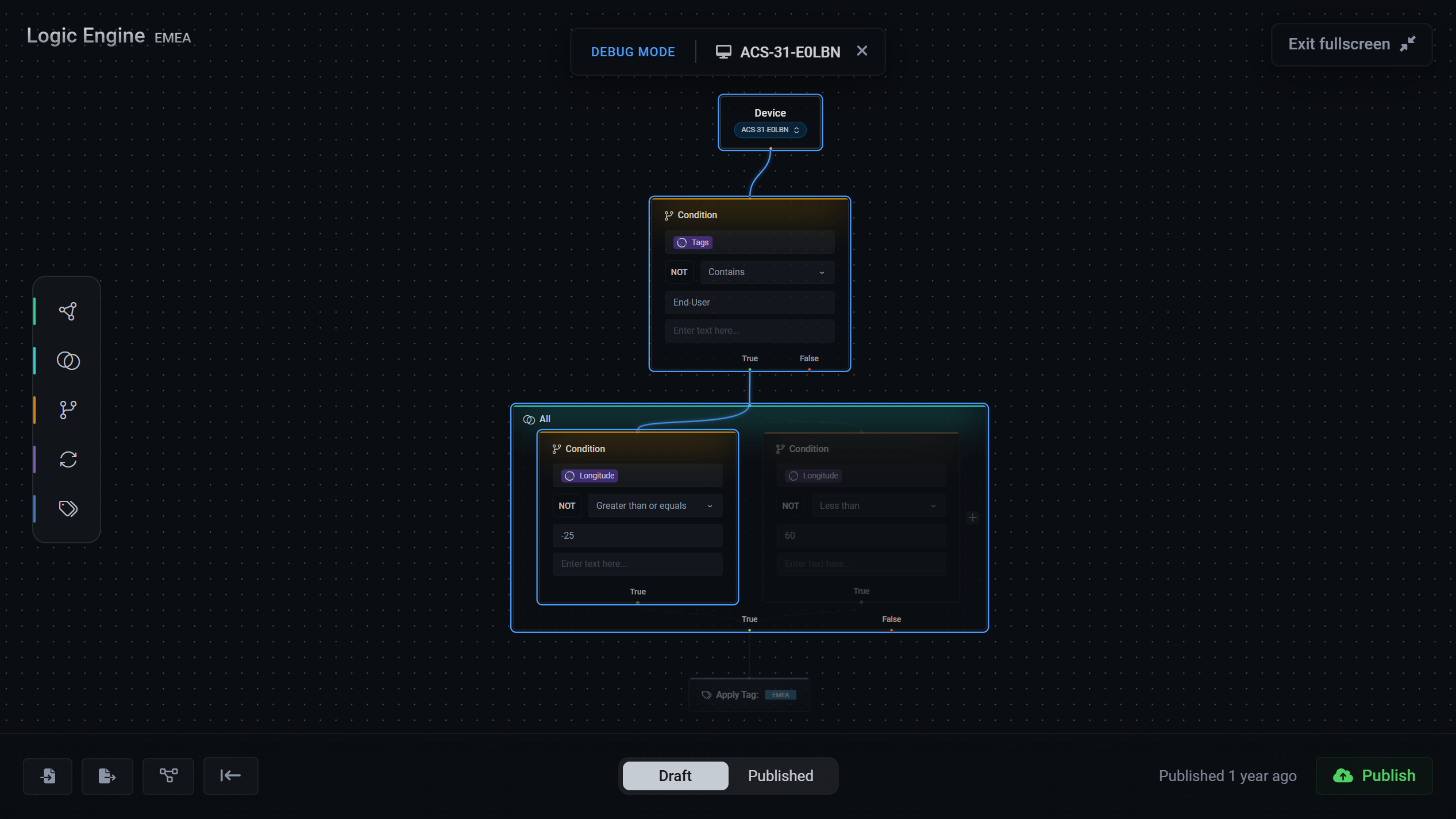
Intelligence & Customisation
Powerful tools to organise and analyse your security data
- Logic Engine: Build sophisticated custom fields and data transformations aligned to your compliance frameworks and security policies.
- Custom Dashboards: Build tailored views for different teams and stakeholders. Executive summaries, SOC dashboards or compliance reports.
- X-Ray View: View raw data from each connected source for complete audit transparency. Verify data accuracy and prove control effectiveness.
- Enhanced Dynamic Columns: Advanced filtering and column customisation for precise data analysis and reporting.
Why Protect Changes Everything
Reduce Mean Time to Remediate
Automated workflows cut remediation time from days to hours, ensuring issues are resolved as soon as they are detected.
Scale Security Operations
Handle 10× more security events with the same team. Automation handles routine tasks so your team can focus on complex threats.
Custom Risk Models
Logic Engine lets you define risk scoring that matches your business. Weight factors based on your industry, regulations and risk appetite.
No-Code App Development
AI Reporting empowers security teams to build custom tools without engineering resources. "Vibe coding" makes complex applications simple.
Demonstrate Security ROI
Track improvements over time with AI reporting dashboards, demonstrating measurable security performance and clear return on investment.
Closed-Loop Security
Protect closes the security loop with detection, remediation, and verified resolution, eliminating manual spreadsheet tracking.
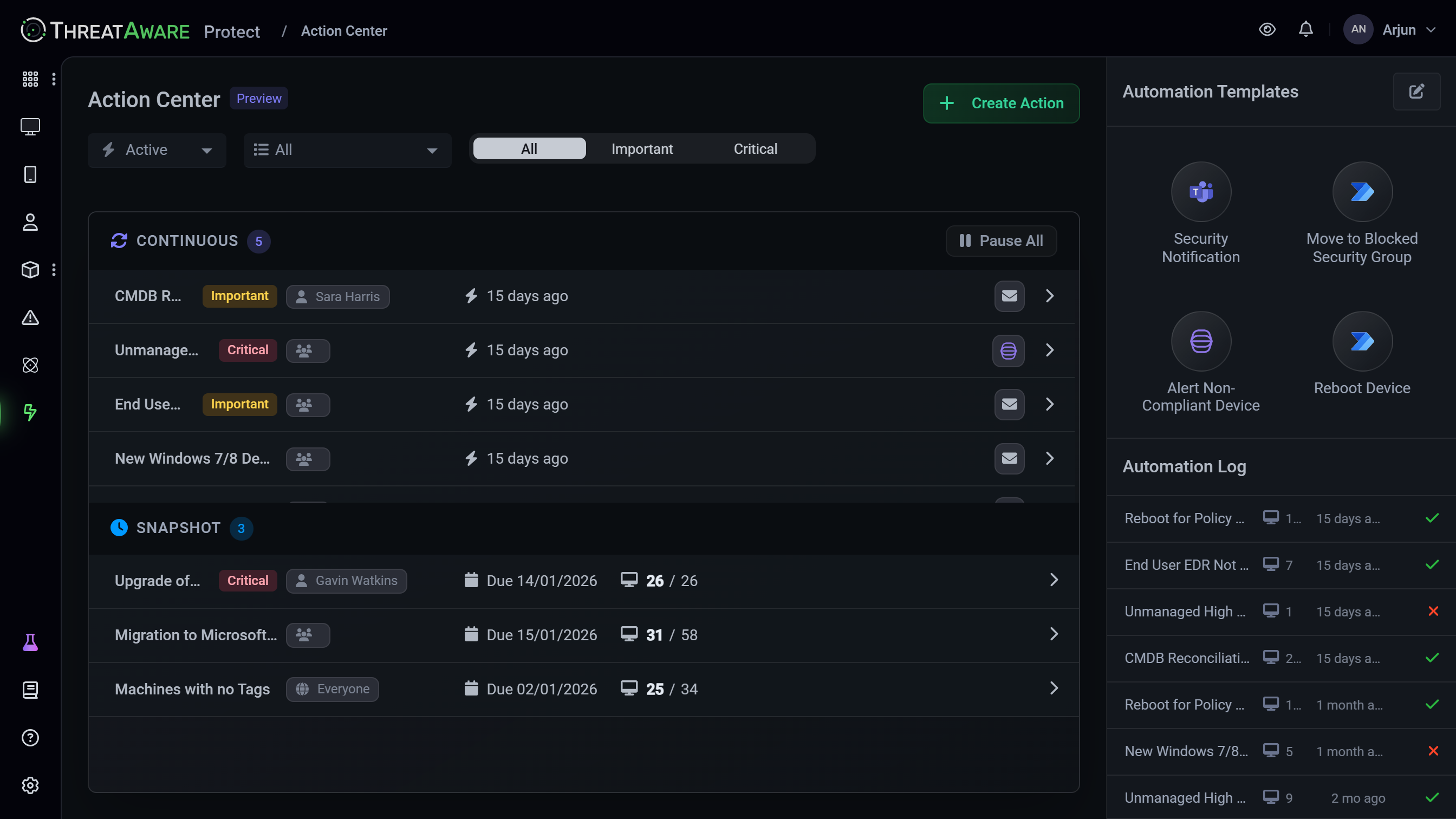
Automated Remediation Workflows in Action
A powerful example of how to use Protect is to streamline security incident response by automating remediation workflows and confirming resolution across your environment.
Detect
Issue identified in real-time
Create Ticket
Auto-generate in ServiceNow/Jira
Notify Team
Alert security team via Slack/Teams
Remediate
Trigger automated fix via Power Automate
Verify
Confirm resolution & close ticket
Detect
Issue identified in real-time
Create Ticket
Auto-generate in ServiceNow/Jira
Notify Team
Alert security team via Slack/Teams
Remediate
Trigger automated fix via Power Automate
Verify
Confirm resolution & close ticket
Remediation Use Cases
Real-world scenarios where automated workflows deliver immediate value.
Missing EDR Response
Instantly detect devices without an EDR, automatically create service desk tickets, notify security teams and track resolution.
Encryption Enforcement
Identify unencrypted laptops, trigger Power Automate workflow to enable BitLocker/FileVault and verify encryption status.
High-Risk Device Isolation
When device risk score exceeds threshold, automatically create incident ticket, notify SOC and optionally trigger network isolation.
MDM Enrolment Drive
Detect devices not enrolled in MDM, notify security team with instructions and track enrolment progress until complete.
Patch Compliance
Weekly scan for out-of-date devices, escalate to patch management team, track patching progress and generate compliance reports.
Executive Reporting
Automatically generate weekly security posture reports with AI Reporting, highlighting improvements and identifying new risks.
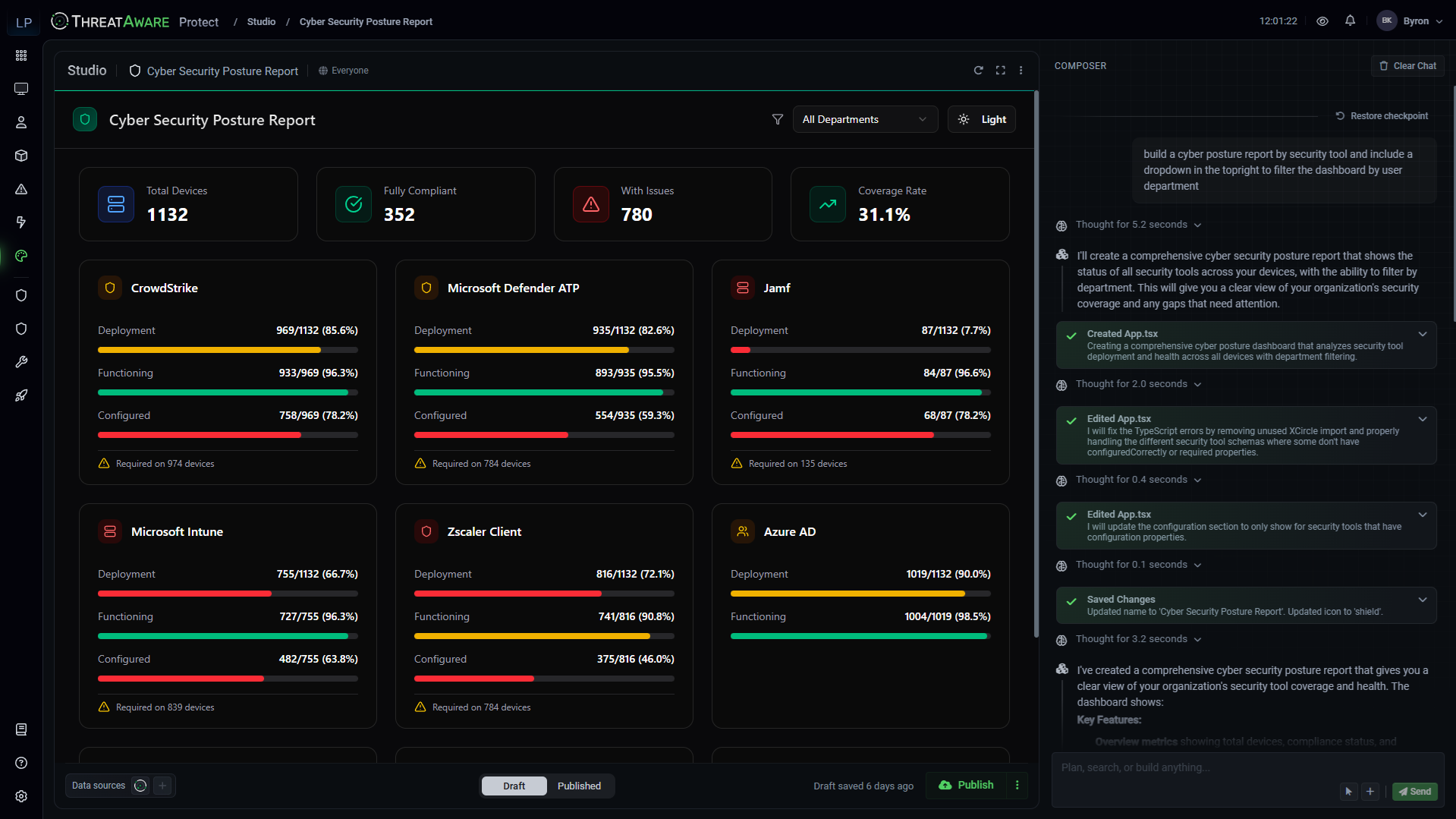
AI Advanced Reporting
Build custom security applications without code.
Our "vibe coding" approach lets security teams create sophisticated dashboards, risk assessments and compliance reports using simple prompts.
Simply describe what you need, and AI generates working applications instantly.
- Visual Dashboard Builder: Create executive dashboards, security risk assessments and user profiles with professional design systems. Real-time data updates and comprehensive visualisations.
- Natural Language Coding: Describe your requirements with simple prompts. AI generates complete applications with advanced logic, data processing and enterprise-grade design.
- Intelligent Risk Assessment: Automated risk scoring algorithms with customisable factors. Track MFA status, login activity, device compliance and more with colour-coded risk levels.
Secure Every Device in Your Network
Instantly uncover and protect every asset in your IT estate with ThreatAware.
Identify unknown devices, reconcile asset data across platforms, and eliminate security gaps to ensure continuous cyber hygiene.
Book a Demo