Jon AbbottAre the Days of Traditional RMM’s Numbered?
For many MSP’s, managing a huge fleet of computers has always been a challenge however with the increase in cyber attacks, it's getting harder.
A typical response is to deploy a Remote Monitoring Management (RMM) tool, which involves an agent being installed on all the computers being supported. However, if any workstations are missed, a client would receive inferior support, their machine may be at risk and your reputation would be tarnished, not to mention the potential loss in revenue if charging by the workstation. There are in fact many challenges when it comes to managing a huge fleet of computers in a secure and profitable way, depending on which software you want to use to protect your clients.
Let’s start with antivirus software. You find a new product that seems to tick all the boxes; it offers the correct level of protection, is cost effective, and easy to use. However, it needs to integrate into your RMM, otherwise you can’t get the report data you need or control it centrally, so you choose one that does integrate with the RMM when you make the final purchase. The following week a new client joins who is midway through a 3-year contract with a different antivirus, that is not supported by your RMM… your single pane of glass has its first crack.
You continue to select and connect additional tools such as Patching for Windows and Macs, Web proxy, and device encryption. The more you connect the more cracks are appearing in your pane of glass, there are now fragments and workarounds everywhere. This starts to have a huge impact on your team’s efficiency as they are flitting between consoles, finding new machines as they go, and not knowing which issue to tackle next.
The dream of automation, systems talking to each other, and other efficiency gains become a distant memory.
A Highly Flexible, Efficient and Secure Alternative
Here at ThreatAware, we are rewriting the rule book for how to manage the vast fleet of computers that you are responsible for on behalf of your clients. Our revolutionary technology is starting to really drive efficiencies – no matter which underlying tools an MSP chooses.
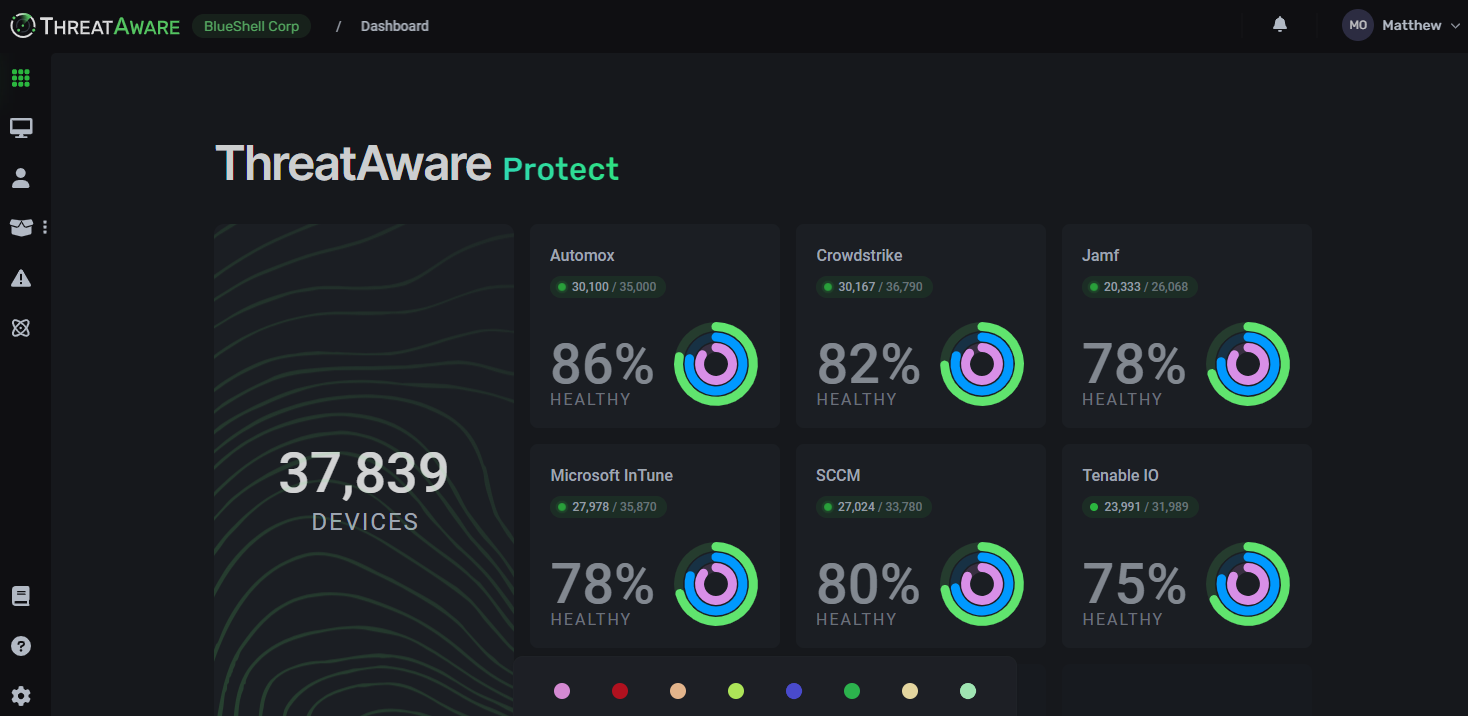
Firstly, it is entirely agentless, you simply connect your systems to ThreatAware and in 10 minutes ThreatAware has found all the computers accessing your corporate apps, networks and endpoint security tools. There is no more guesswork or asking your clients for inventory lists, ThreatAware does all of the searching for you. ThreatAware connects to over 80 tools including nearly every endpoint security tool on the market.
It doesn’t matter if each client has different antivirus products, it doesn’t even matter if a single client has multiple antivirus products. ThreatAware will connect to, analyse the data and report on any incidents or events within your security tools.
Now that everything is in one place, the real power of ThreatAware can be utilised. ThreatAware allows the MSP the freedom to choose the best of breed security and utility tools to monitor and manage from a single pane of glass.
Let’s look at the functions a typical MSP requires to professionally manage their client’s systems.
Essential
- Remote control
- Patching monitoring
- AV monitoring
- Hardware inventory
- Software inventory
Advanced
- Remote scripting
- Internet browsing protection
- Encryption verification
- Darkweb scanning
That is a large number of functions and the more advanced MSP’s will have even more. Even if we just take the first five essential items, although lots of RMM’s will perform all these functions, you will nearly always have to compromise. For example, remote control is typically handed over to a third party, or if it is native it will not work on Macs or isn’t as feature rich as a dedicated solution such as TeamViewer. The patching and the antivirus monitoring will generally be via an agent and be highly restricted to a couple of vendors, maybe just one.
Hardware and software inventory is done by the same agent, however sometimes there is no Mac support, so you need another product to do that. The limitation of course is, as with all agent based products, the RMM can only see workstations where the agent is installed.
As we start moving into the more advanced items, remote scripting is critical if you want real efficiency, and although lots of RMM’s cater for this, many try to put a heavy GUI on top which makes them slow and cumbersome. The final three are typically done by third party tools. Encryption verification can be integrated with the RMM, but Browsing Protection and Darkweb scanning are not. That is another two consoles that you need to authenticate with and check separately.
The ThreatAware Way
There are some critical points about ThreatAware which make it so refreshing:
- Product agnostic
- Highly integrated
- Agentless
Product Agnostic
With ThreatAware being product agnostic and not charging more regardless of how many products you connect, that single pain of glass becomes a reality. Far more than just a single pain of glass, every tool you connect enriches the data of the platform for your other connected tools to benefit from. For example, if you connect in three of your antivirus products ThreatAware adds all of those machines to the hardware inventory. It will then validate those machines against all of your other controls such as patching and encryption. This approach means you can literally find the best tool for the job for every task.
Highly Integrated
The reason I say highly integrated is because there are two ways of accessing your data. Firstly you can login to ThreatAware and see all of your computers in the hardware inventory, all of the apps in the software inventory and the status of all the security tools. If you need to remote onto a machine just click connect and your chosen remote connection will allow you to, in fact if you have a couple for backup reasons, they are all there at a click of a button. As all of the authentication can be done via Office 365, you can essentially always be logged into ThreatAware.
The integration goes to the next level with our Chrome extension. When activated it brings all of the rich data from within ThreatAware to any other system. For example if you have a service desk system with the name of the computer you need to support the ThreatAware mini menu appears and allows you to see its security status, who is logged in and you can remote onto that machine with a single click.
I feel I need to write this again, as this level of integration and efficiency cannot be matched. Anytime one of your client’s computer names appears on any website you can remote onto it at a click of a button.
Agentless
Here’s One I Made Earlier
With our product agnostic approach you can choose from a nearly endless list of tools. Below is an example combination of tools which give you an idea of how versatile ThreatAware is and how you can choose best of breed every time, without sacrificing efficiency:
- Remote Control Windows & Mac– TeamViewer
- Antivirus Windows – Bitdefender
- Antivirus Macs – Malwarebytes
- Antivirus Linux – Sophos InterceptX
- Hardware Inventory Windows – Action1, Bitfender
- Hardware Inventory Mac – Addigy, Malwarebytes
- Software Inventory Mac – Addigy, Malwarebytes
- Service Desk – Freshservice
- Windows Patching – Manage Engine
- Mac Patching – Automox
- Remote Scripting Windows – Action1
- Remote Scripting Mac – Addigy
- Internet Protection – Cisco Umbrella
- DarkWeb scanning – DarkWebID
- Encryption verification – Action1
This combination of products without ThreatAware would be a mishmash of random tools, with no synergy, efficiency or overall visibility. However, with ThreatAware they are all tied seamlessly together, all combining their data to enhance the overall picture. Computers can be controlled directly through the ThreatAware console or even from the individual management consoles through the ThreatAware Browser extension.
The end result is that clients are running the most secure setups with zero gaps in their defences and a team of engineers rapidly connecting via ThreatAware, thus providing the best combination of security and support capability.
With the number of attacks increasing exponentially this approach is the way to keep you and your client’s businesses thriving.
Ready to protect all your assets?
Leveraging its proprietary timeline-matching technology, ThreatAware ensures you have a complete, accurate, and non-duplicated asset inventory in real-time. No more guesswork – spot and fix deficiencies across your entire IT estate instantly.
Onboard in less than 30 minutes.
Request a Trial