Richard MitchellBreak Down Security Siloes and Control Cyber Assets via a Single Pane Of Glass
The average enterprise has been forced to take on an ever-increasing number of security tools to keep up with today’s threat environment.
At last year’s RSA, Matt Chiodi of Palo Alto Networks estimated that even smaller companies are using an average of 15-20 different security tools, with the number going up to 50-60 for medium sized enterprises and more than 130 for large organisations.
With so many different vulnerabilities to account for and such a wide range of potential cyber attacks to detect and defend against, a good spread of security tools is essential.
However, a large arsenal of tools can be a double-edged sword if each of these solutions is siloed and operating independently from the rest.
More Tools, Less Time
Let’s look at an example with a bare minimum of 10 different security tools, each with its own separate dashboard. Checking alerts and updates for each one will take an IT security professional roughly 20 minutes. Added together, it will take nearly three and a half hours to get through all of them. Almost half the working day gone, and only the most basic of security activity to show for it.
Combine this with other daily IT and security duties, fighting fires and responding to user requests, and there is very little time left for any of the strategic, high-value activity that is so essential for improving an organisation’s security maturity.
Having all these siloed tools also makes it difficult to get an accurate view of the company’s overall security standing. Each tool provides a limited view into its own area of speciality, whether that might be email security or malware detection. Taken together the result is an array of puzzle pieces that the security team must spend time fitting together to get the full picture.
Hardly an ideal situation for a team that is already rushed off its feet getting through their daily checklist of tasks and putting out fires. Key activity like carrying out security audits and reporting to the board can be arduous tasks to be dreaded.
Puzzling Through The Pieces
Worse still, fitting together the puzzle pieces will waste crucial time in the event of an active cyber attack. If the team is forced to flit between a half dozen different tools to get to grips with an attack in progress, the threat actor will have a huge head start in executing their attack.
Organisations must break down these silo walls if they are to reclaim this lost time and have a chance of keeping up with fast-paced cyber attacks. However, unless they are published by the same vendor, tools looking at different fields will rarely lend themselves to interoperability with each other.
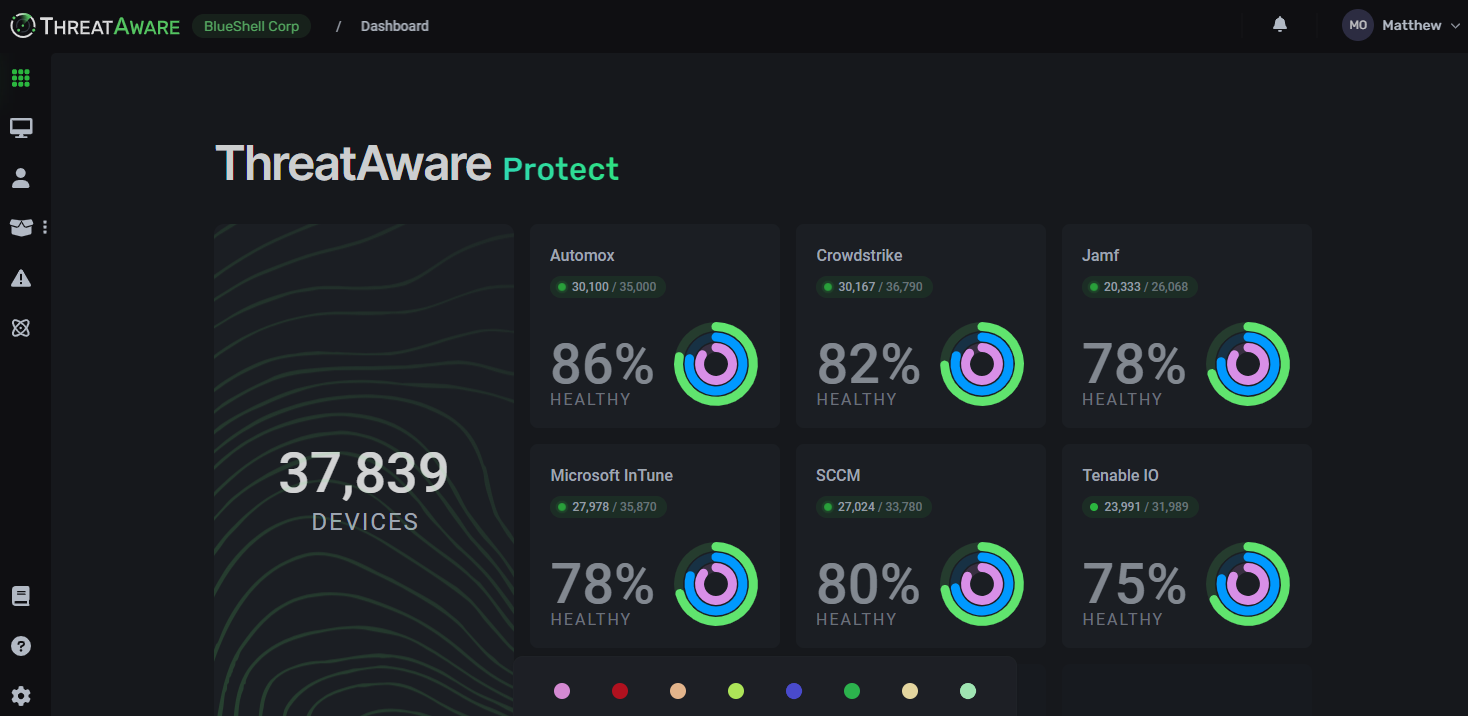
The answer is to tie the entire suite into a single platform, providing the IT security team with a central dashboard to monitor and control all their solutions together. The previously fractured view of disparate alerts and intel can be easily viewed through a single pane of glass, making it far easier to see the full picture of cyber risk. Essential daily activity can be automated from a single point of control, saving multiple hours every day.
Ready to protect all your assets?
Leveraging its proprietary timeline-matching technology, ThreatAware ensures you have a complete, accurate, and non-duplicated asset inventory in real-time. No more guesswork – spot and fix deficiencies across your entire IT estate instantly.
Onboard in less than 30 minutes.
Request a Trial